Beyond the Checkbox Pentesting That Finds Real Threats
Human-led, Canadian pentesters, and a purpose‑built Portal to accelerate remediation. Audit‑ready evidence and compliance mappings that unblock enterprise deals


High-growth SaaS companies
CTOs and engineering leaders at high-growth SaaS companies face security challenges that slow growth

SMBs & Enterprises
CISOs and product leaders at SMBs and enterprises face pentests that waste money and fail to deliver

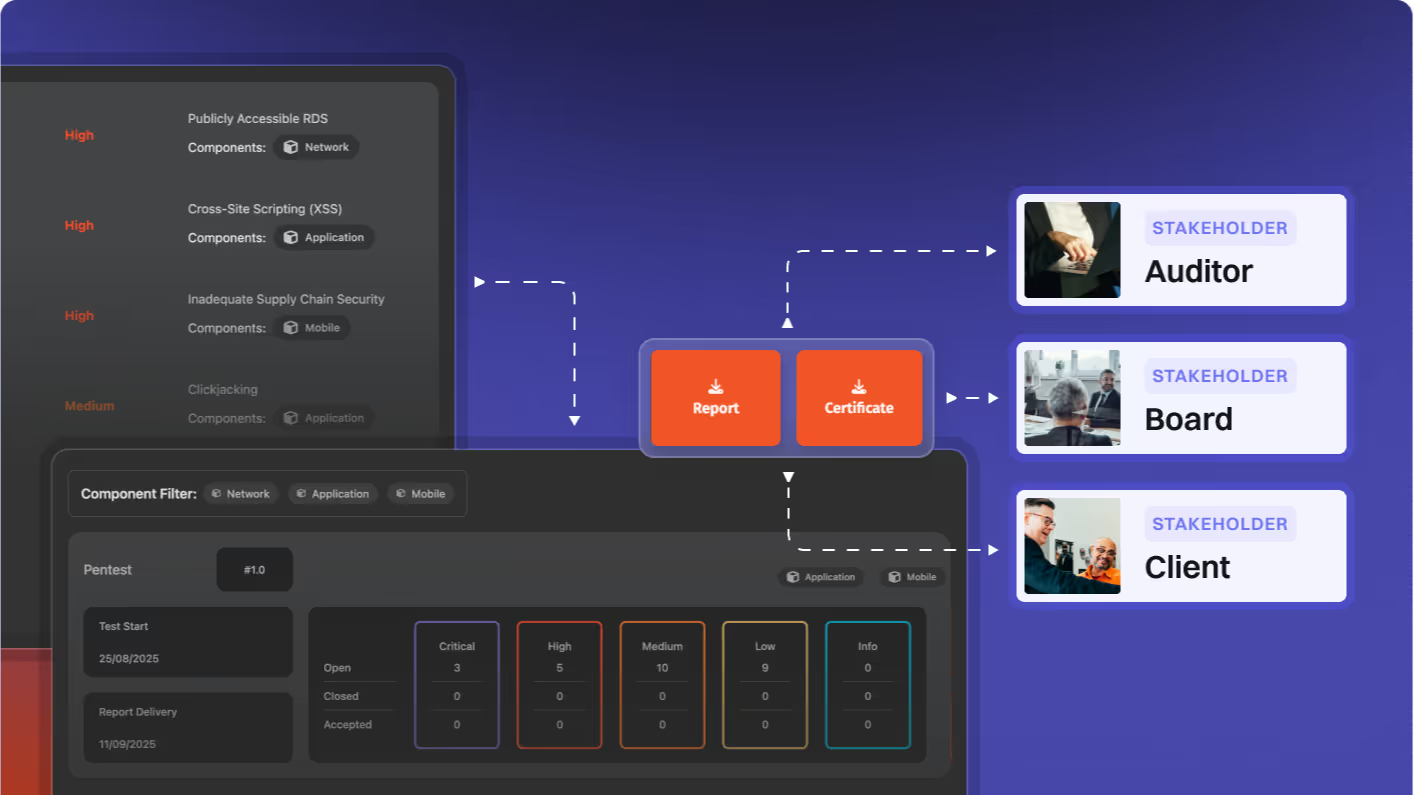
Our reports help clients demonstrate security and earn credibility with Fortune 500 companies.
Why Software Secured?
Software Secured delivers manual, exploit-driven pentesting with built-in retesting and audit-ready evidence - helping tech teams reduce risk, accelerate compliance, and close enterprise deals faster
Manual-first, attack surface secured
Human-led pentests uncover risks that scanners miss
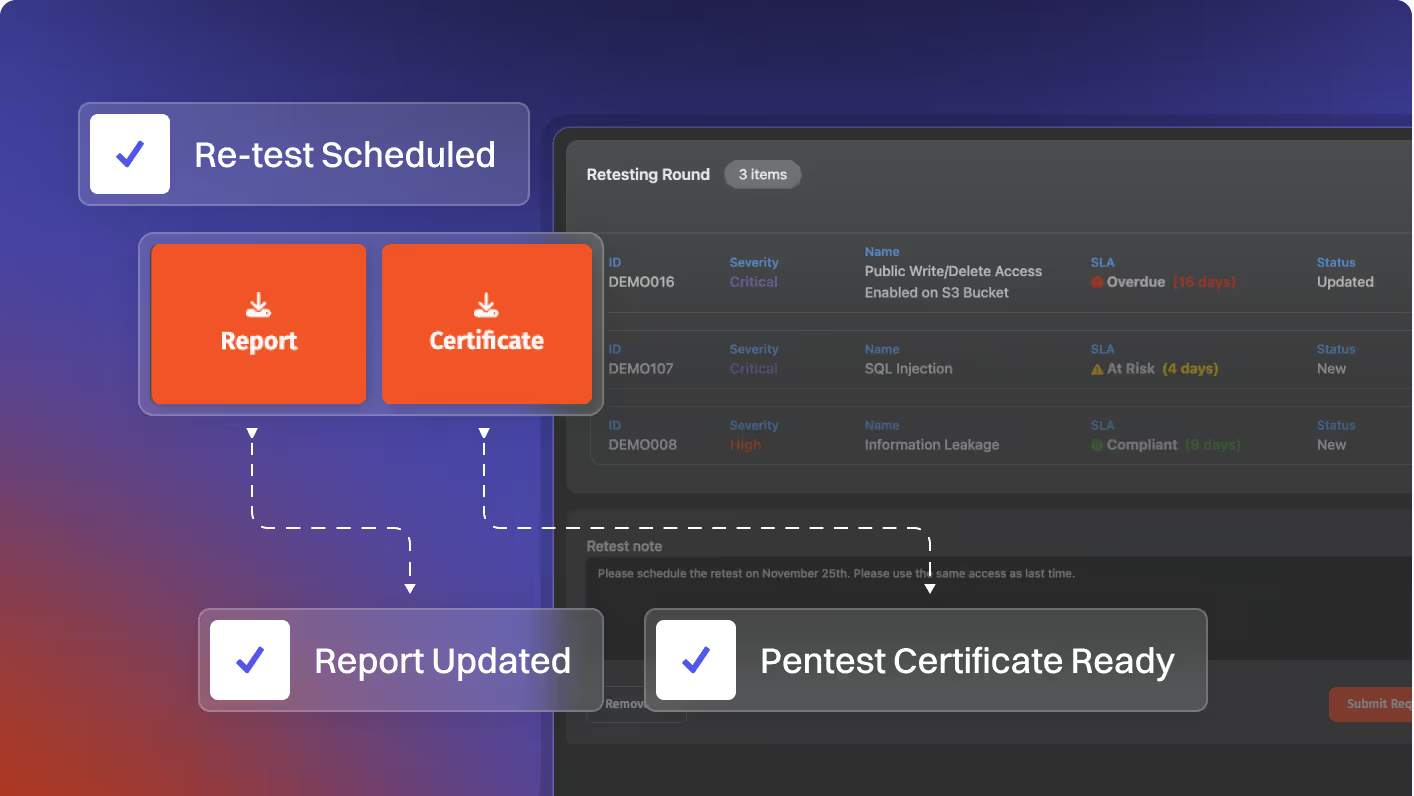
True partnership through remediation
Support doesn’t stop at uncovering vulnerabilities
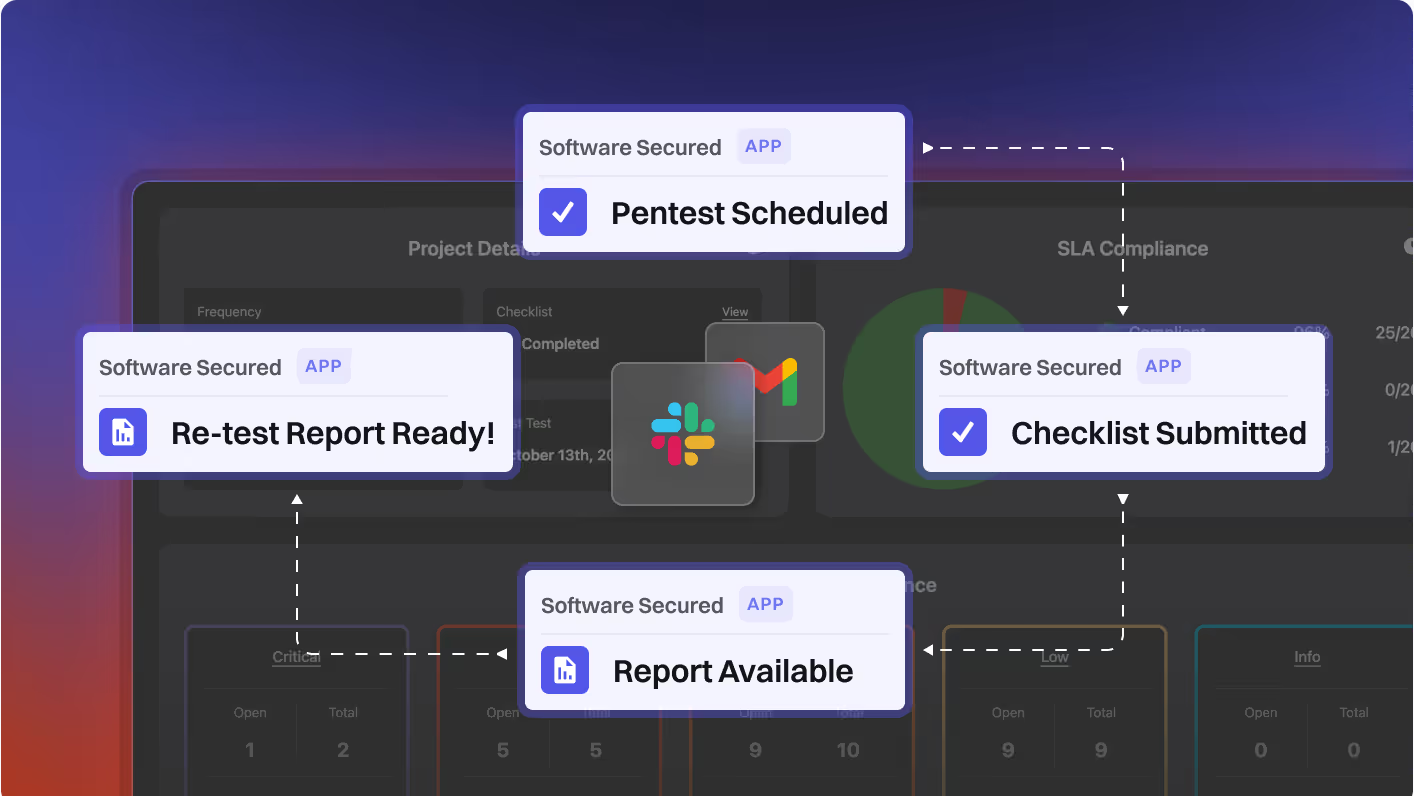
Portal clarity for leaders
The Software Secured Portal provides executive clarity
Full-time certified hackers
Dedicated Canadian pentesters conduct your testing
Our Specialties
Web, API & Mobile Security
We uncover exploitable flaws in web, mobile, and APIs. Our secure code reviews and manual testing identify logic bypasses, chained attacks, and hidden vulnerabilities that scanners miss.


Infrastructure & Cloud Security
Our pentesters validate networks and cloud infrastructure, uncovering misconfigurations, lateral movement, and segmentation gaps. Prioritized evidence helps reduce incidents, speed up audits, and meet regulatory requirements with confidence.


AI, IoT & Hardware Security
We secure AI, IoT and hardware technologies with specialized testing. From AI prompt injections to IoT and hardware flaws, our evidence strengthens resilience and ensures security compliance confidence for innovative companies.


Advanced Adversary Simulations
Red teaming and threat modelling reveal systemic risks. We simulate attacker behaviour, deliver prioritized exploit evidence, and help executives reduce business impact, regulatory exposure, and board-level uncertainty.


Penetration Testing as a Service
PTaaS delivers ongoing, manual pentests aligned to release cycles. Unlimited retesting avoids security bottlenecks. Premium Portal features help close deals faster, keep compliance current, and demonstrate measurable business risk reduction, without the overhead.


OWASP Top 10 Training
We train developers on critical application risks. Learning from real security breaches, teams gain practical skills that reduce vulnerabilities, improve security maturity, and shift security left while obtaining compliance.


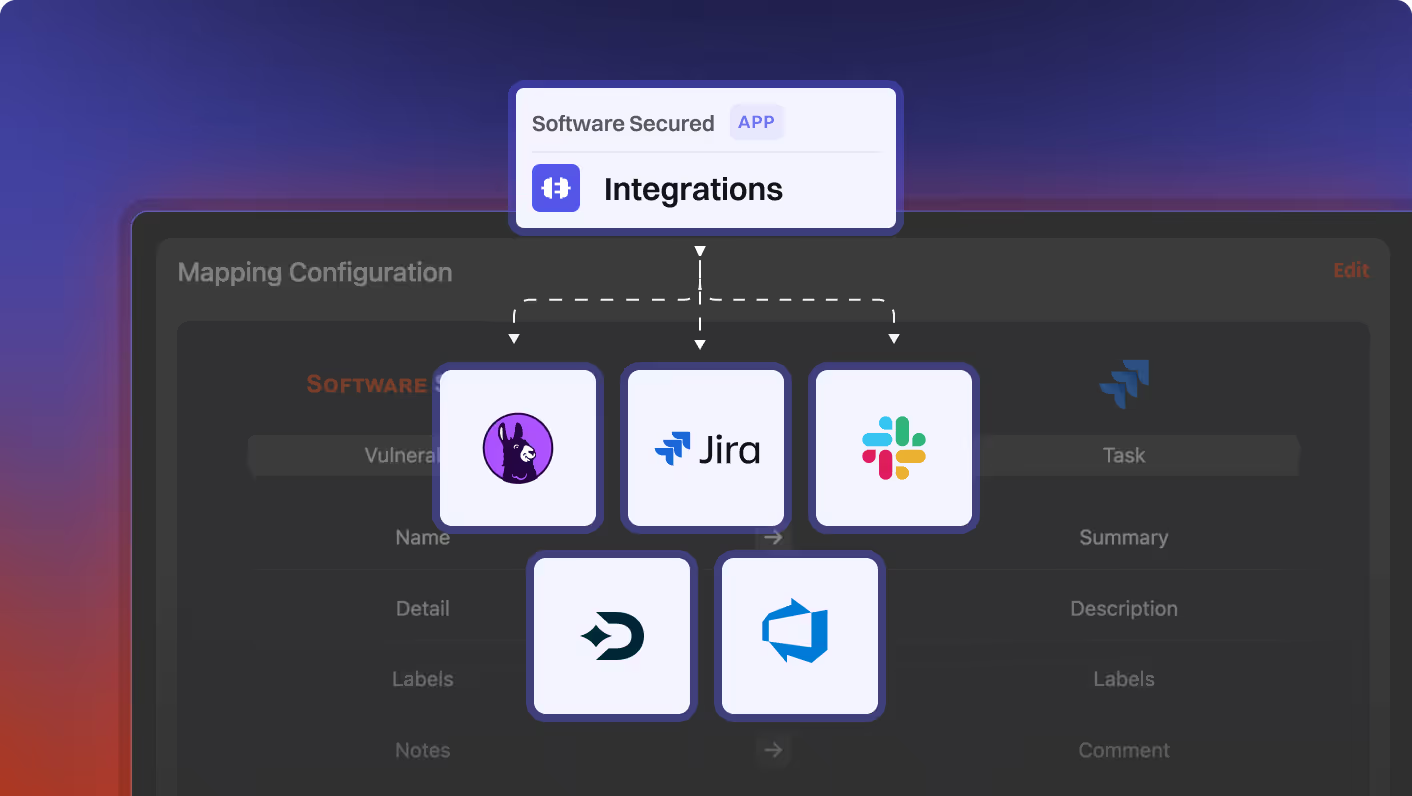
Portal: A Platform That Turns Findings Into Fixes
Track progress, close gaps faster, and give executives the visibility they need to make security investment decisions
Unveiling our customers' success stories.
Our comprehensive penetration testing and actionable reports have 0 false positives so you can identify, understand and solve security gaps faster
Trusted by high-growth SaaS firms doing big business:

“We were able to use the reports from Software Secured to demonstrate to our board we had reduced the threat level on the risk registry”

Of all vulnerabilities found by Software Secured are critical or high severity
How it Works
Consultation Meeting. Our consultants span five time zones. Meetings booked within 3 days.
Customized Quote. Pricing tailored to product scope and compliance needs. Quotes delivered within 48 hours.
Pentest Scheduling. Testing aligned to your release calendar. Scheduling within 3-6 weeks - sometimes sooner.
Onboarding. Know what to expect thanks to Portal and automated Slack notifications. Onboarding within 24-48 hours.
Pentest Execution. Seamless kickoff, and minimal disruption during active testing. Report within 48-72 hours of pentest completion.
Support & Retesting. Request retesting within 6 months of report delivery. Auto-scheduled within 2 weeks.
Resources from our team

10 Best Cybersecurity SaaS Companies Protecting Cloud-First Businesses
The cybersecurity SaaS market is crowded and confusing. Many tools promise one-click safety yet ship noisy dashboards that do not plug into developer workflows.
.avif)