Understanding Your Attack Surface: How to Measure Endpoints in Your Application
Learn more about how to measure your endpoints for your penetration testing scope and endpoint security best practices for your organization.
Studies show a 400% increase in endpoint cyber threats over the last several months of 2022, it's increasingly important for organizations to be aware of their attack surface and take measures to protect their assets. One way to do this is by conducting penetration testing. Penetration testing is a simulated cyber attack against your applications and systems to check for exploitable vulnerabilities that are found in endpoints and more. When you're getting a penetration test scoped, you're likely going to be asked about how many endpoints you have to get the full picture of your attack surface.
In this blog post, we'll explore how to measure your endpoints for your penetration test scope and why organizations must understand their full attack surface. We will also uncover endpoint management best practices to help you improve your overall security posture. But first, let’s dive into the endpoint infrastructure.
What are endpoints?
In the context of software and APIs, an endpoint is typically a specific URL that accepts particular types of requests. It represents a resource that can be accessed or manipulated by a client application. For example, in a web API that provides access to a database of products, the endpoints might include:
- /products - returns a list of all products\n- /products/{id} - returns information about a specific product identified by {id}
- /products/update/{id} - updates the information for a specific product identified by {id}
- /products/delete/{id} - deletes a specific product identified by {id}
Each of these URLs represents an endpoint that clients can use to interact with the API and access or modify resources.

API endpoints are URLs that receive requests from clients and return responses from the server. These endpoints allow the client application to interact with the server application by sending HTTP requests to specific URLs. API endpoints can be used to retrieve data, update data, create new data, or delete data. For example, an e-commerce website's API might have endpoints such as
- "/products" to retrieve a list of products
- "/products/123" to retrieve a specific product
- "/cart" to add items to a cart
- "/checkout" to complete a purchase.
Traditionally, these endpoints can be accessed using a variety of HTTP methods, including GET, POST, PUT, DELETE, and more. Each HTTP method corresponds to a specific action, such as retrieving data, creating new data, or deleting data.
Why measure endpoints?
Endpoints are an essential part of any web application, as they provide a means for users to interact with the application. However, from a security perspective, endpoints can also be a significant vulnerability. 94% had some security issues with their production APIs over the past year, followed closely by authentication problems at 40%. When it comes to preparing for your penetration test, endpoints are a key component in determining your attack surface. As endpoints are a large entryway for threat actors, penetration testers will conduct numerous tests in attempt to detect any potential vulnerabilities. Knowing the endpoint infrastructure during the preparation phase allows both your development team and the penetration testers to assess the full extent of your application surface, and make sure that no stone is left unturned.
Here are some reasons why endpoints are important for penetration testing:
Identify potential attack vectors
API exploits have increased by 286%. In a study carried out by the Gartner security research team, they were able to analyze 17,500 security reports to manually distinguish 193 API exploits. From the first to the second quarter of 2022, it increased from 50 to 142 exploits each quarter, which is about a 3x increase. Endpoints that are critical to the functionality of an application tend to be the most likely to be targeted by an attacker, especially endpoints that access, store or process sensitive data, as exploiting these endpoints tends to have the most serious impacts and security implications.
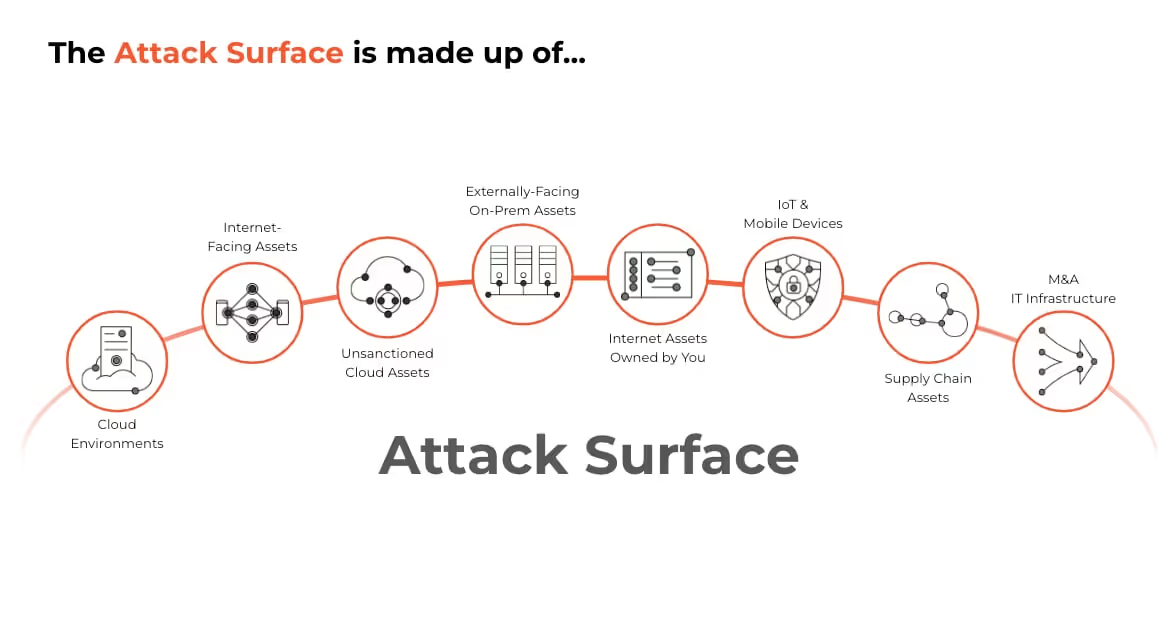
Endpoints are a key component of the attack surface of any application. In a survey done by Salt Security, 77% of respondents said their existing tools aren’t very effective in preventing API attacks.
By identifying and cataloging the endpoints in your application, you can identify potential attack vectors and get a better understanding of your overall attack surface before a penetration test. Beyond a penetration test, identifying potential threats can help your organization evaluate where there can be better security integrations in your application and SDLC. Becoming familiar with your endpoint infrastructure and secure best practices learned from your penetration test report, allows your developers to implement secure coding practices before code hits production.
Determine the scope of the penetration test
Measuring endpoints also helps determine the scope of the penetration test. By identifying all of the endpoints in your application, you can determine which endpoints contain more sensitive data than others, and which endpoints have a higher exploitability risk. The majority (95%) of organizations have experienced an API security incident in the past 12 months, according to Salt Security’s Security Report. By identifying and understanding the API landscape, testing can be prioritized and allocated toward this rapidly growing threat. At Software Secured, we ensure endpoint infrastructure is scoped before every penetration test to ensure comprehensive coverage.
How to measure endpoints
There are two main methods for measuring endpoints: manual and automated.
Manual method
The manual method involves listing all the endpoints in the application's code. This can be time-consuming and error-prone, especially for large and complex applications. However, you also may have a deeper insight into the API functions and business context, paired with daily use cases from the team.
To do the manual method, developers can start by reviewing the application's code and listing all the URLs that handle HTTP requests. Developers can also check the server logs to identify the URLs that are being accessed by clients. Once all the URLs are identified, developers can organize them by functionality and create documentation. Endpoint documentation should be reviewed and updated regularly to maintain awareness of the attack surface and to facilitate scoping pentests and other application security services and tools.
Automated method
The automated method involves using specialized tools to automatically detect and measure endpoints in the application. These tools can save time and reduce errors but may result in a lack of depth and business context.
There are several endpoint measurement tools available, such as Postman, Swagger, and Insomnia. These tools can automatically scan the application's code or API documentation and attempt to identify all of the endpoints. To use automated tools, developers can install and configure them to scan the application's code or documentation.
Best practices for secure endpoint management
To ensure accurate endpoint measurement, developers should follow some best practices. Here are 3 useful tips for endpoint management:
Create and update the endpoint documentation regularly
Creating and continuously updating endpoint documentation is the best, easiest, and most efficient way to conduct secure endpoint management. Your organization should update the endpoint documentation regularly, especially after making significant changes to the application's code or functionality. This can help ensure that the documentation is accurate and up to date. You can add an endpoint documentation audit or update whenever a new feature, piece of code or functionality is introduced into your application. Integrating these audits and updates regularly, allows developers to have continuous knowledge surrounding endpoint management.
Validate any user-supplied input that endpoints can receive
Validation is the action of checking or proving the validity or accuracy of something or an object, in this case, a user input data. Validating user-supplied input is an important step in securing your application and preventing malicious attacks such as injection attacks or cross-site scripting (XSS) attacks. Here are some general steps you can take to validate user-supplied input:
Define a set of validation rules: Define a set of validation rules that define the acceptable format and type of the input. For example, if you're expecting an email address, you can define a rule that checks whether the input contains a valid email format.
Validate the input: When the user submits the input, validate it against the defined validation rules. If the input does not match the validation rules, return an error message to the user.
Sanitize the input: Sanitize the input by removing any characters or strings that could be used in an attack. For example, if the input is a string that will be used in a SQL query, sanitize the string by removing any SQL injection characters.
Use type checking: Use type checking to ensure that the input is of the correct type. For example, if you're expecting a number, check that the input is indeed a number.
Use parameterized queries: If you're using a database to store user-supplied input, use parameterized queries to prevent SQL injection attacks. Parameterized queries ensure that the input is treated as data and not as executable code.
Use third-party libraries: Use third-party libraries that provide validation and sanitization functions for common types of user input, such as email addresses, URLs, and phone numbers.
The key to validating user-supplied input is to define a set of rules that define the acceptable format and type of the input, and then validate and sanitize the input against these rules.
Regularly scan your application and run code reviews to ensure that no endpoints remain unknown and insecure.
To regularly scan your application and run code reviews to ensure that no endpoints remain unknown and insecure, you can follow these steps:
Perform regular penetration tests: Conduct quarterly penetration tests on your application to identify any vulnerabilities or weaknesses that may exist in your application's security. This will help you identify any potential security gaps that may exist in your application and endpoint infrastructure. When a new endpoint or API is added to your application's attack surface between penetration tests, is it important to keep these additions or changes documented to update your penetration testing provider before your test.
Conduct regular code reviews: Conduct regular code reviews to ensure that your application's source code is secure and free of vulnerabilities. Developers can catch security issues early on in the development process with code reviews, and catch potential vulnerabilities before they become more significant and costly problems in production. Code reviews can also help ensure that developers are following security best practices, such as input validation and parameterized queries, which are essential for securing endpoints.
Integrate security into your SDLC: Adopt a secure software development life cycle (SDLC) to ensure that security is a part of your application's development process from the start. This involves integrating security into each phase of the development process, from design to testing and deployment. Implement general security best practices, such as input validation, parameterized queries, and password hashing, to ensure that your application and respective endpoints are secure.
By following these steps, you can regularly test your application and run code reviews to ensure that no endpoints remain unknown and insecure. This will help you identify and address any potential security vulnerabilities or weaknesses in your application, and improve your application's overall security.
Conclusion
Endpoints are an essential part of web development and APIs, but they can also be a vulnerability for applications. With the rapid rise of API endpoint breaches, understanding and monitoring your endpoints is necessary for scoping penetration tests, and overall understanding your attack surface. At Software Secured we are dedicated to providing you with quality in-depth comprehensive tests derived from our scoping practices to ensure maximum coverage and vulnerability prevention. Book a call with our team to dive deeper into understanding your attack surface and reducing endpoint risk.

.avif)



