One Platform to Manage Every Pentest
From scheduling to remediation to compliance, the Software Secured Portal gives engineering, security, and IT leaders control in one place.
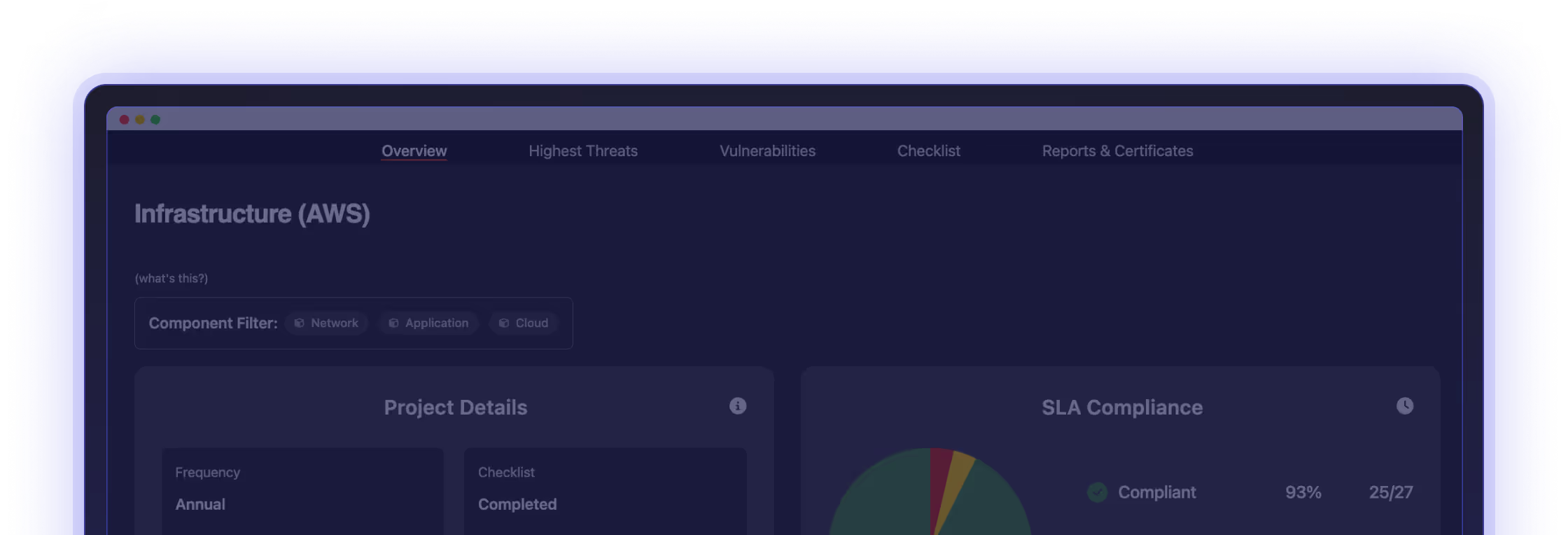
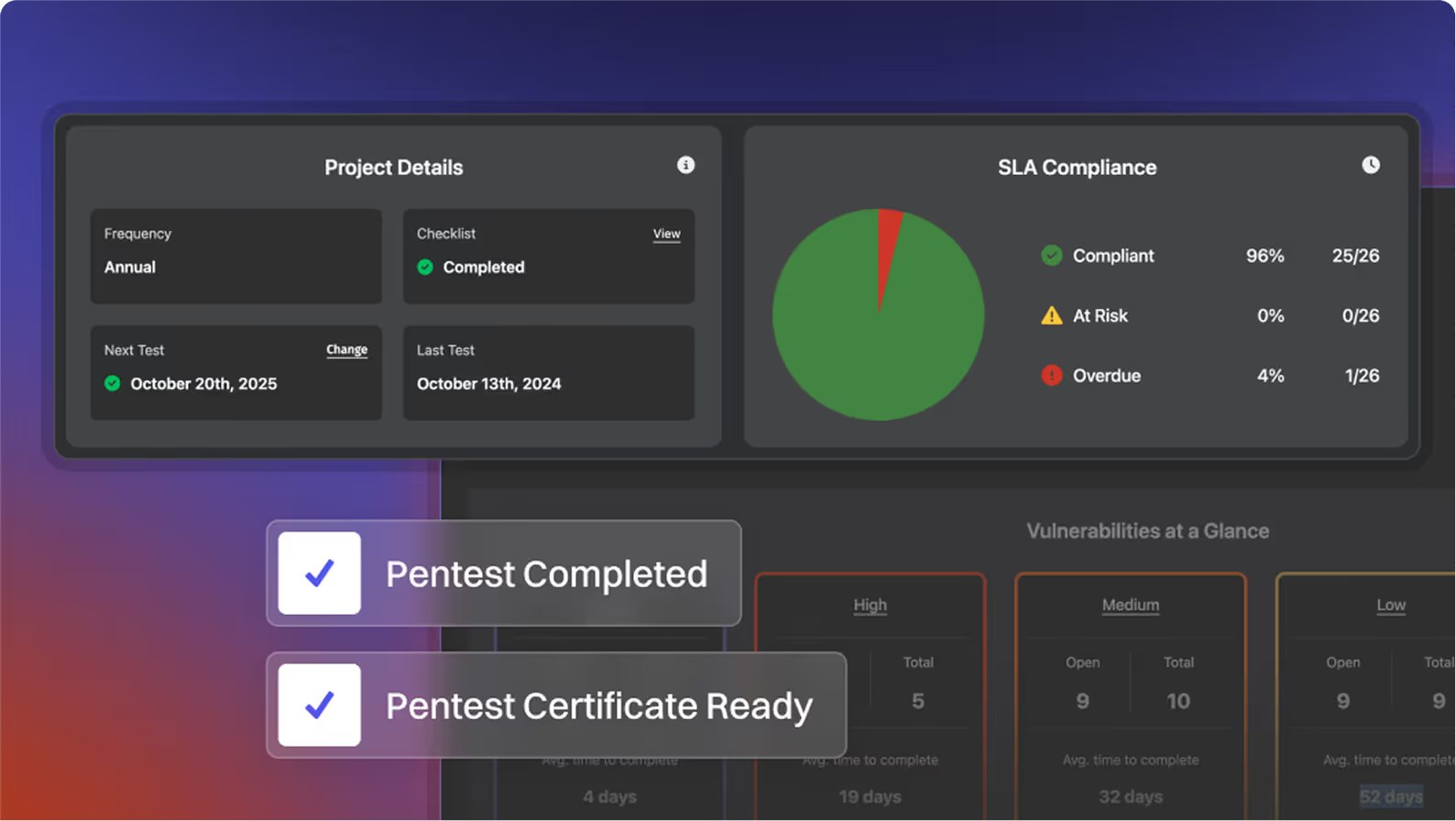
Frictionless Pentest Management
Engineering &
Compliance Automation
Security You can Trust
Single Tenant Architecture
Every client has a dedicated environment, isolating your data from others
Encryption at Rest
All stored evidence and reports are encrypted with AES-256
Encryption in Transit
TLS 1.3+ protects data moving between users and Portal
Automated Key Rotation
Cryptographic keys rotate automatically, reducing exposure risk
Granular RBAC
Assign roles and limit access down to the feature level
SSO Authentication
Integrate with Okta, Azure AD, or Google for enterprise-ready login
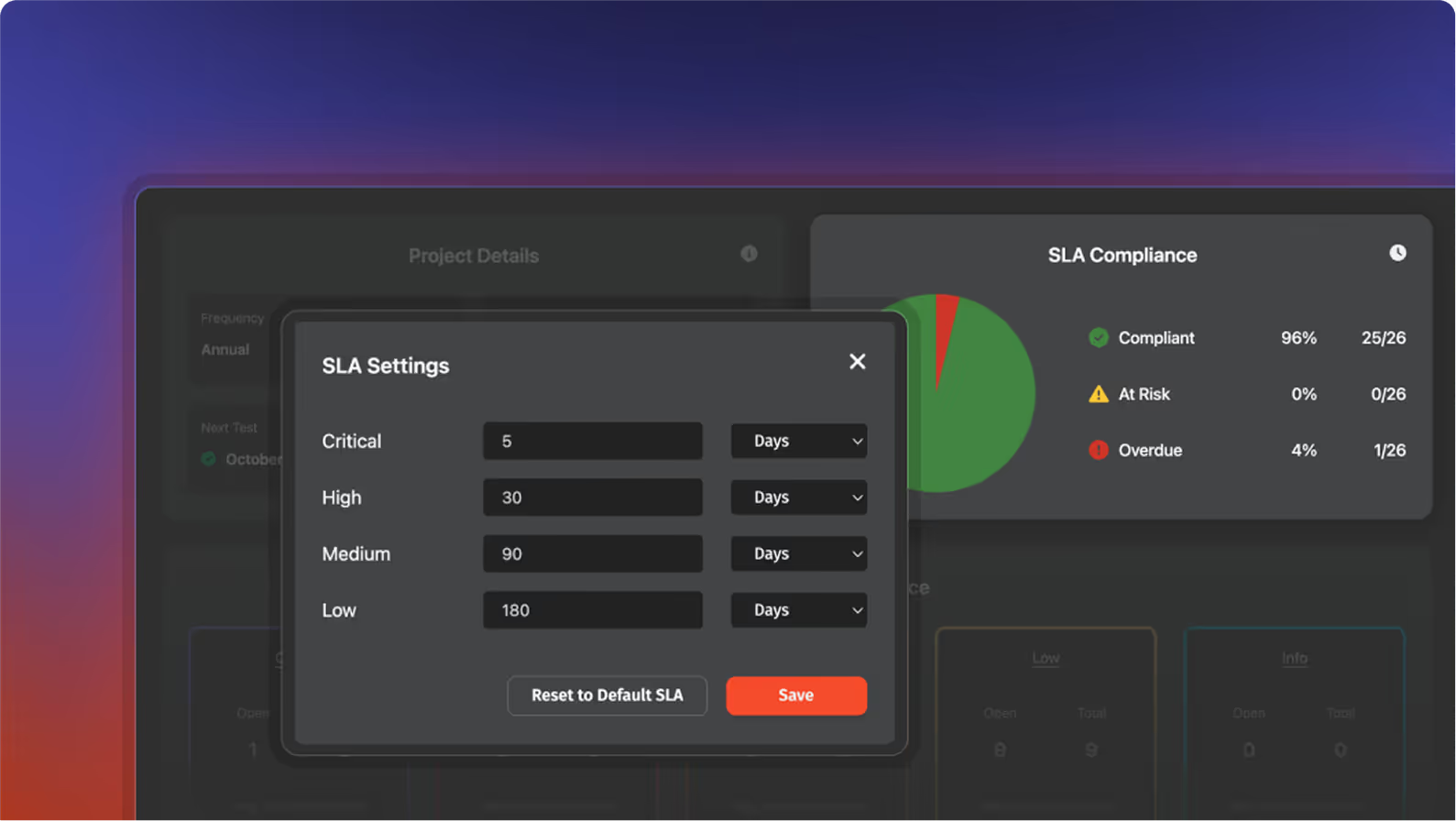
Quarterly Pentesting
Portal itself is pentested every 90 days. Security you can verify
SOC 2 Certified
Independent audit proof your data is handled to the highest standards
Integrations That Matter to You
Slack
Push real-time findings directly into team channels
Azure DevOps
Link vulnerabilities to work items inside sprint planning boards
Jira
Export issues with PoCs and severity in one click
Vanta
Automatically sync remediation reports in your Documents section
Drata
Continuous audit readiness directly into your compliance workflows
Trusted by Leading SaaS, FinTech, HealthTech
“Software Secured's dashboard and reports were also intuitive and perfect for a company like mine.”
Security Made Easy. Get Started Now.

Frequently Asked Questions
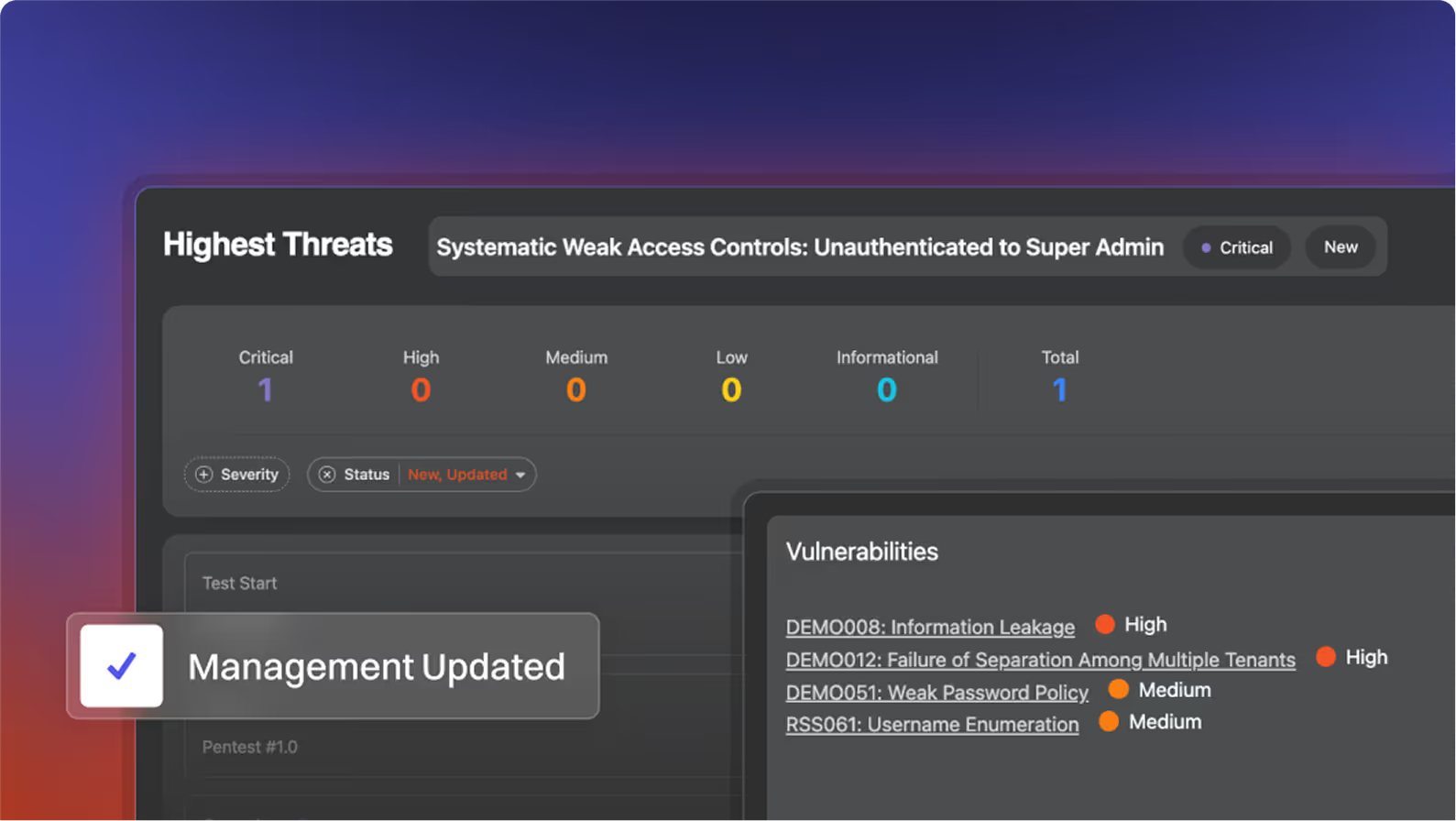
How do I access and track vulnerabilities in the Portal?
All vulnerabilities are logged with full exploit evidence. You can filter by severity or component and export reports anytime
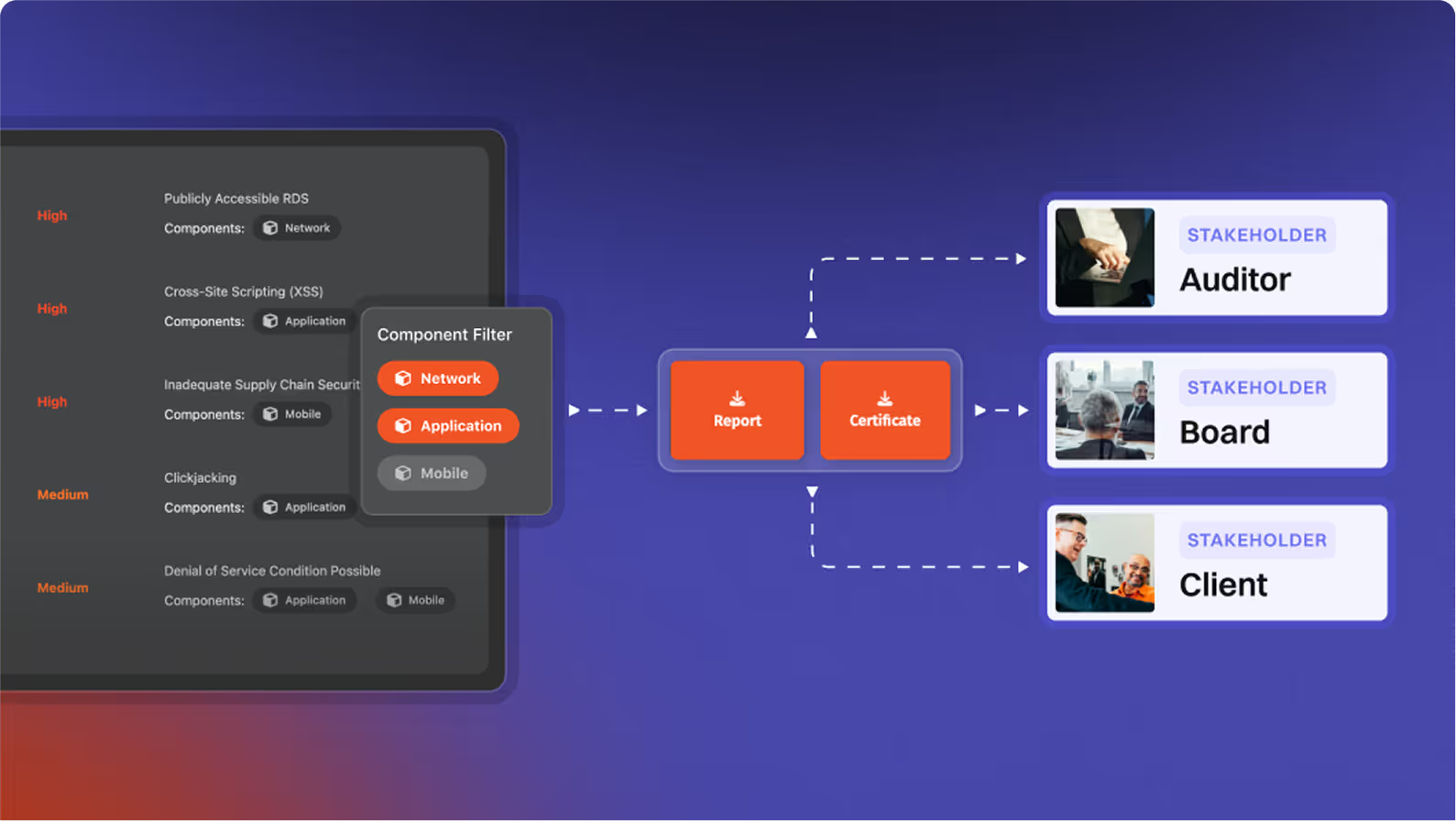
How do retests work in the Portal?
When your engineers apply a fix, you can request a retest with a single click. The retest is scheduled automatically, our team validates the fix, updates the evidence, and the Portal reflects the closure
How is scope managed in the portal?
The portal tracks assets in scope, versions every change - scope drift is transparent and documented
How is access to sensitive findings controlled?
Portal supports SSO, role-based permissions, audit logs, and evidence redaction so only the right people see detailed exploit data
How are findings presented to execs and developers?
Findings include risk-based prioritization, exec summaries, reproducible PoCs, and developer-ready remediation steps. Exports available (PDF)