4 Ways Security Leaders Uses Penetration Testing to Elevate Their Security Programs
Learn more about the ways penetration testing can help security leaders elevate their security program, and 4 ways to track success.
Did you know that companies that have experienced a breach underperform the market by more than 15% three years later?
Check Point Research reported that it found 50% more attack attempts per week on corporate networks globally in the calendar year 2021 compared with 2020. Maturing your security program is becoming increasingly important as cyber threats continue to increase at a rapid rate.
Penetration testing is a tool that can help security leaders take their security program to the next level by identifying vulnerabilities and improving the overall security posture of their critical systems. In this article, we will explore the important role that penetration testing plays in a security program, the top benefits and ways of integrating penetration testing into your security programs, and how to measure the success of your security program's maturity. With the increasing frequency and sophistication of cyber attacks, regular penetration testing is becoming essential for businesses to stay ahead of the curve. So, how can penetration testing help your organization mature its security posture?
Understanding the Role of a Security Program in Protecting Your Organization
Customer and client data security has never been more important, and maturing your security program is one of the best ways to reduce the likelihood of a data breach. A security program is a set of policies, procedures, and guidelines to help an organization identify, assess, and manage information security risks.
A typical security program includes elements such as risk management and assessment, security controls, incident response plans, and employee training. Essentially, your security program is the full, multi-faceted security strategy and governance that protects your organization’s sensitive data and capabilities.
Exploring the Benefits of High-Assurance Penetration Testing for Enhanced Security Measures
High assurance penetration testing is a type of security testing that is used to evaluate the security controls of an information system or an application. These penetration tests use in-depth, and comprehensive methodologies and advanced tools to identify potential security vulnerabilities. They go beyond checking the box and more into the business logic, custom attack scenarios, advanced exploitation and attack chaining techniques. There are various areas in which you can identify a high assurance penetration test compared to a checkbox
- The way scoping is done and how thorough it is
- Whether any kind of threat modeling is included which indicates understanding the business logic.
- Testing methodology and whether it follows any industry standards such as OWASP Top 10, NIST, ASVS, etc.
- Reporting and how thorough, comprehensive, and accurate it is
- Remediation and how extensive it is
Scoping for penetration tests is a key component for understanding your complete attack surface. Gathering information about your application before your penetration test helps to map out potential attacks that could be used on your application based on its infrastructure and components.
For proper penetration testing coverage, specific information should be gathered such as the network assets in scope, backend endpoints, authentication types/methods in scope, and the number of roles in scope to name a few. In our experience, these scoping questions are the best way to accurately assess the effort required for proper coverage. In tandem with our scoping, our penetration tests are manually tested by a team of ethical hackers to find more vulnerabilities than typical automated approaches. The manual approach allows our team to explore and mimic behaviors and thought patterns similar to a real threat actor, to make sure all possible exploits are explored further.
Industry standards are a very important part of a mature penetration testing methodology. It ensures proper coverage, depth, and proof to stakeholders that enough testing rigour has been exercised against the application/system. For example, at Software Secured, we test against 5 industry standards.
Scoring vulnerabilities is another important aspect, different penetration testing vendors use different approaches. Relying on an industry standard ensures objectivity is used to score vulnerabilities, something all stakeholders can agree on and get behind. For example, at Software Secured, we use CVSS and DREAD for fairly calibrated issue scoring.
Comprehensive reporting includes detailed reproduction steps, as well as remediation recommendations, to ensure that your developers have all the help they need to fix vulnerabilities faster. A high-assurance penetration test team should be on standby for any additional help and extended application security strategies during the remediation process. Consultative approaches should be used to help your team gain the necessary skills to understand their security blindspots as well as proactively mitigate security risks in the future.
Here’s a quick summary of the factors of a high-assurance pentest:
- It can be more costly due to resources, time, and effort.
- Considers the context of the target and attackers’ thought processes in attacking the system.
- Reporting is detailed along with helping with prioritizing the fix.
- Help with custom remediation along with an insight into the attack process.
In addition to high assurance, there are also some aspects that the company should take care of such as regular audits and reminders to resolve SLA. These components of a penetration test make up the differences between a good and bad quality penetration test. Learn more about what to look out for in a high-quality penetration test here.
Recognizing the Critical Role of Penetration Testing in Strengthening Security Programs
The average cost of finding vulnerabilities in the design phase is approximately $500.00. When vulnerabilities are caught in an earlier stage via penetration testing, developers have the opportunity to understand, digest and learn where their coding errors arose from, and how to avoid them in the future. When vulnerabilities are caught at a later stage, the costs are increased exponentially. The cost to fix vulnerabilities in the maintenance stage is 100 times more than the cost of finding a vulnerability in the design phase. By integrating penetration testing early into the SDLC, you can remediate vulnerabilities faster and more cost-efficient than those who have lower security integrations. Having a strong security program helps your organization ensure the confidentiality, integrity, and availability of your client and customer information, as well as the organization’s private data through effective security management practices and controls. Let’s dive into the best ways you can integrate penetration testing into your security program, and its unique benefits.
Implementing the Top Strategies to Enhance Security Programs Through Penetration Testing
Demonstrating Value to Stakeholders Through Penetration Testing Results
Usually, security teams face a bunch of challenges as they launch security programs. One of the main challenges is proving value to stakeholders. Another challenge is quantifying the return on investment to upper management. Proving the value to developers as they are the main contributors to any security program. Finally, proving to product teams that slight delays to fix a zero-day would be worth it to avoid a reputation crisis if that zero-day was exploited.
Penetration testing provides a practical way to quickly prove value to stakeholders. A high assurance penetration test would outline practical ways hackers can get access to data, the probability of that happening and what exactly could happen. Here is an example:
Let's take an example of a social media application, the application allows users to upload their profile pictures, but there is no validation which leads to “Unrestricted Upload of File with Dangerous Type” being cited in the pentest report. The pentesters were able to upload an ASPX (.net) file instead of a usual picture. Not only that, they were able to find where the file was uploaded to the server and execute it. A good penetration testing report should mention exactly the impact, how to reproduce it and the evidence.
The following screenshot shows exactly what the attacker would be able to achieve, this would resonate well with technical C-Level and product teams.

The following screenshot shows the exact location and steps required to replicate the vulnerability

Finally, the following screenshot is evidence of how the file is uploaded and the results of the attack, where the attacker can simply scan the server and easily elevate their privileges from there to own the target server.

Enhancing Developer Knowledge and Skills Through Penetration Testing Insights
Most developers’ security training consists of Computer Based Training (CBT). Being cost-effective, and scalable with diversified topics, makes them a very popular option among security teams. The downside is that developers watch the videos, mostly a few hours long in total, once a year to prove compliance. This does not give the developers the information they need to make their code more secure. The interaction with penetration testers post-test could be one of the best educational experiences. According to a Harvard blog, there are 4 different learning styles: Auditory, Visual, Communicative and Kinesthetic.
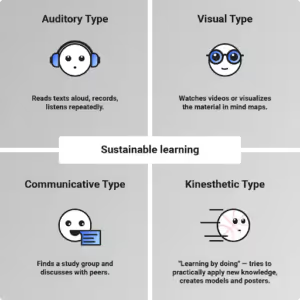
Source: https://blogs.harvard.edu/learnmegood/which-type-of-learner-are-you-and-which-learning-style-fits-you-the-best/
Auditory learning: reads text aloud, records, and listens repeatedly.
Visual learning: watches videos or visualizes the material in mind maps.
Communicative learning: finds a study group and discusses with peers.
Kinesthetic learning: learning by doing - trying to practically apply new knowledge.
If the majority of your developers are communicative or kinesthetic learners then working with pentesters could be a great way to drill down the concepts that they learned from the secure coding videos.
Interacting with the pentesters, asking questions, and debating ideas are great ways for communicative and kinesthetic learners.
Validating Security Programs Through Comprehensive Penetration Testing
A typical security program, any program, will follow the rule of diminishing returns.

The productive phase: This is where all the friction with other stakeholders is, but all the gains as well. Gains in terms of establishing and improving security controls, processes and practices.
The diminishing returns: This is a point where additional input or improvement will give you a slower gain in output. This does not mean there are no more risks or all the risks that have been mitigated, it usually means that additional controls have less impact on the overall risk reduction.
Negative returns: this is the point in a program where additional controls/processes will lead to negative returns, perhaps because of overhead, duplicate results or something similar.
Penetration testing can change the curve of diminishing returns.

Penetration testing would show which components of the program are working and which parts of the program are not working. Additionally, it would uncover security gaps that are handled by any control. Here are a few examples from our experience with Software Secured clients:
- A Penetration Testing as a Service client where they have a web application where security has been built into the application from Day 1. The application is tested every quarter. Lots of security controls are built into the design, implementation, testing, and deployment phases. During one of our penetration testing exercises, we discovered that a developer added a backdoor to the database where they could edit the database directly without authentication. A huge security gap in the security program.
- Another example where a client who had a very mature program and wanted to use penetration testing techniques to test whether their tools would pick up a stealth attack.
Driving Positive Change Through Effective Penetration Testing Practices
What happens if you find yourself in a culture of security denial? Some of the verbal symptoms of such a culture are:
- “We don’t store sensitive data, hackers won’t gain anything.”
- “We have SOC2, why do we need to do anything extra?”
- “We never had an incident, why should we prevent against a non-existent scenario”
- “Security is a necessary evil, we should be doing the absolute minimum so that we don’t hinder our productivity and progress”
If any of the above sounds familiar, you might be a part of a culture of security denial. The bad news is within this culture building a security program might be an uphill battle, where you would be viewed as the person who…
- Prevents progress.
- Paranoid for no reason
- Does not “get” how real business is being done
The good news is that the culture of security denial is reversible, it will just take time. Changing this culture requires a bunch of things: education, evidence, constant communication, and influence. One of the things that we have seen accelerate is a high-assurance penetration test. The results of such a test bring the theoretical attacks closer to home. Showing everyone a simulation of what would happen if an actual hacker would target their applications/networks. Additionally, hearing it from a neutral entity who is also an expert in the field always holds weight.
Tracking the Success of Your Security Program: 4 Key Metrics to Monitor
The return on investment (ROI) of high-assurance penetration testing is easy to prove, but difficult to see immediately. With preventative measures, the best case scenario is that no data breach occurs, meaning there is no big celebratory moment like when sales hit quota, or a product team launches a new release. All departments within your organization will have different goals, and you must speak to these organizational goals with metrics that prove true value for all parties.
There are 4 key metrics you can use to track the success of your security program:
- Impacts of higher risk vulnerabilities
- Vulnerability density trends
- Open-to-remediated ratio and triage efficiency
- Remediation effort costs
Analyzing the Impact of High-Risk Vulnerabilities on Security Programs
Tracking the impacts of risk for vulnerabilities is essential in helping organizations understand the potential impact of a successful attack on their systems. By identifying and prioritizing vulnerabilities based on their level of risk, organizations can allocate their resources effectively to address the most critical vulnerabilities first.
For each critical or high vulnerability found on your penetration test report, associate a dollar value to it. You can do this by calculating the estimated legal fees, fines, lost revenue, and wasted employee salaries, for example.
When you track the impacts of severe risks, you can compare the breach risk cost to the cost of remediation, to determine ROI.
Breach risk ($) is equal to breach likelihood (%) multiplied by breach impact ($).
This calculation can be great for giving a ballpark estimate of the potential breach risk your company could face based on a certain vulnerability.
ROI is equal to the potential breach risk ($) divided by the cost to fix the breach OR breach risk after patching. To get ROI in percentage multiple ROI x 100.
By using a combination of the breach risk and ROI equations, you can estimate the potential breach damage of a particular vulnerability and the ROI of a security investment. If your impacts of severe risks are reduced over time, this can be a good indication that your security program is maturing.
Identifying Trends in Vulnerability Density to Improve Security Measures
Vulnerability density is the number of vulnerabilities per unit of code, and tracking this metric over time can help organizations identify trends in their security posture.
To determine your vulnerability density trends, your team needs to analyze how many vulnerabilities (of all scores) you have discovered in an average year and track specific security mitigations that could have been put in place to reduce this number over time. If you conduct more than one penetration test per year, you can change this number to track how many vulnerabilities are found per penetration test.
The vulnerability density is given by:
VD +V / S
where S is the size of the software and V is the number of vulnerabilities in the system. Following the common practice in software engineering consider 1000 source lines as the unit code size.
If the vulnerability density decreases after a penetration testing engagement, this can be a clear indicator that the organization's security posture has improved. Furthermore, tracking vulnerability density can help organizations identify areas of their codebase that are particularly vulnerable, allowing them to focus their penetration testing efforts where they will be most effective. This allows for an accurate understanding of how the vulnerability density is being reduced over time with penetration testing and contributes to your overall security program maturity.
Optimizing Triage Efficiency Through Open-to-Remediated Ratios
On average, it takes 8 days for a vulnerability to be weaponized after it is found by a hacker. It takes the average development team around 202 days to patch these issues. By tracking the open-to-remediated ratio of vulnerabilities, companies can identify gaps in their remediation process and address them promptly to minimize the window of vulnerability.
DID YOU KNOW: Quarterly penetration tests reduce staff time spent by 69 minutes of triage per vulnerability, which is an average of 29 hours per pentest.
By tracking your triage efficiency alongside the open-to-remediated vulnerabilities, your organization can determine how effective, how fast their response time is, and how long it takes to remediate a vulnerability. This can also help determine if the Security Level Agreement (SLA) adherence rate is on par, or if there needs to be adjustments made based on this rate. Quarterly penetration testing should reduce this ratio, therefore improving your overall security program maturity.
Managing Remediation Costs Effectively for Sustainable Security Programs
Remediation effort costs are the costs associated with addressing vulnerabilities that are identified during a penetration testing engagement. You can track these costs with the following equation:
Personnel costs ($) multiplied by the hours (hrs) spent
Effective quarterly penetration testing allows for vulnerabilities to be caught earlier in the development stage when aligned properly with the agile framework.
The cost to fix a vulnerability in the production phase is 100 times more costly than fixing a vulnerability in the design phase. This means the average cost of $500.00 to repair a vulnerability in the design stage is multiplied by 100. On average, Software Secured finds 26 vulnerabilities per test. If an organization does quarterly tests, you can save over 4.4 million dollars annually. Tracking remediation effort costs can help determine where resources need to be allocated, and reduce the overall costs of a security program when used correctly.
Tracking and using these metrics allows you to monitor and make improvements to your security strategy, and in turn, improve your overall security program maturity along the way.
Conclusion
Maturing your security program can be a challenge for security leaders, but it is a worthwhile investment due to the increase in cyber threats globally. When it comes to maturing and elevating your security programs, the key to success is proactiveness. Implementing and integrating security into your organization’s existing SDLC ensures that vulnerabilities are found before they hit production and before a hacker can exploit them. Penetration testing is a great tool to mature your security program and take a proactive approach to preventing potential data breaches. You can use the tracking methods to determine which areas need improvement and which are showing progress. The combination of the proactive approach and continuous tracking allows you to mature your security program while allocating time, money, and resources to the right areas. Did you know there are 5 ways penetration testing can reduce your overall security costs? Read our “5 Ways Penetration Testing Reduces Overall Security Costs” to learn more. 4 ways security leaders use penetration testing to elevate their security programs can take a proactive approach to preventing potential data breaches.
ration testing to elevate their security programs can take a proactive approach to preventing potential data breaches.

.avif)



