Comparison of STRIDE, DREAD & PASTA
Learn and compare three popular threat modeling frameworks: STRIDE, DREAD, and PASTA to help you choose the right framework for you.
TL;DR:
- The blog post compares STRIDE, DREAD, and PASTA threat modelling frameworks.
- STRIDE is simple and suitable for small organizations, DREAD is quantitative and for mature security practices, while PASTA is comprehensive and ideal for large organizations.
- Factors to consider when choosing a framework include complexity, use case, output, and ease of use.
- Each framework has its strengths and weaknesses, and the choice depends on the organization's specific needs and circumstances.
- A combination of these frameworks may be used for more effective and comprehensive threat modelling.
Threat modelling provides a systematic framework for identifying, assessing, and mitigating potential security threats within systems, applications, or networks. This approach's primary advantages include enhancing security by proactively addressing vulnerabilities before they are exploited, prioritizing risks based on their potential impact, and guiding the implementation of effective security controls.
Moreover, threat modelling fosters stakeholder collaboration, improving the understanding of security risks across various teams and aligning efforts toward shared objectives. This methodology also assists in optimizing resource allocation by concentrating on the most critical risks, ensures compliance with industry standards, and supports the ongoing improvement of the security posture throughout the development lifecycle.
There are three popular threat modelling frameworks: STRIDE, DREAD, and PASTA. Let's examine these frameworks and how they can improve security.
The STRIDE Framework
STRIDE stands for Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. Threat actors can exploit each of these categories as a potential attack vector.
- Spoofing: Refers to an attacker impersonating a legitimate user or system to gain access or deceive others.
- Tampering: Involves unauthorized modification of data or systems, such as changing values or altering code.
- Repudiation: Deals with denying an event or action that has taken place, which can be used to hide malicious activity.
- Information Disclosure: This involves exposing sensitive information to unauthorized parties, which can be used to exploit or harm individuals or organizations.
- Denial of Service: Refers to disrupting or preventing authorized access to systems or resources, often by overwhelming them with requests.
- Elevation of Privilege: This occurs when an attacker gains higher levels of access or privileges than intended, allowing them to perform unauthorized actions or access sensitive data.
The STRIDE framework systematically analyzes various categories to identify potential threats and vulnerabilities. It categorizes these identified threats into specific classes. For instance, spoofing attacks involve impersonating another user or system, while tampering refers to modifying data either in transit or at rest.
This approach is particularly beneficial for organizations planning to mitigate entire classes of threats by using controls tailored to each class rather than focusing on individual threats.
For example, deploying a Web Application Firewall (WAF) can mitigate an entire class of web application vulnerabilities. By analyzing these categories, organizations can identify potential threats and prioritize them for mitigation.
STRIDE is primarily used for application security, but it can also be applied to network security. The STRIDE framework offers a structured and systematic approach to threat modelling. This helps organizations consistently identify potential threats and vulnerabilities, enhancing their security efforts' effectiveness.

The DREAD Framework
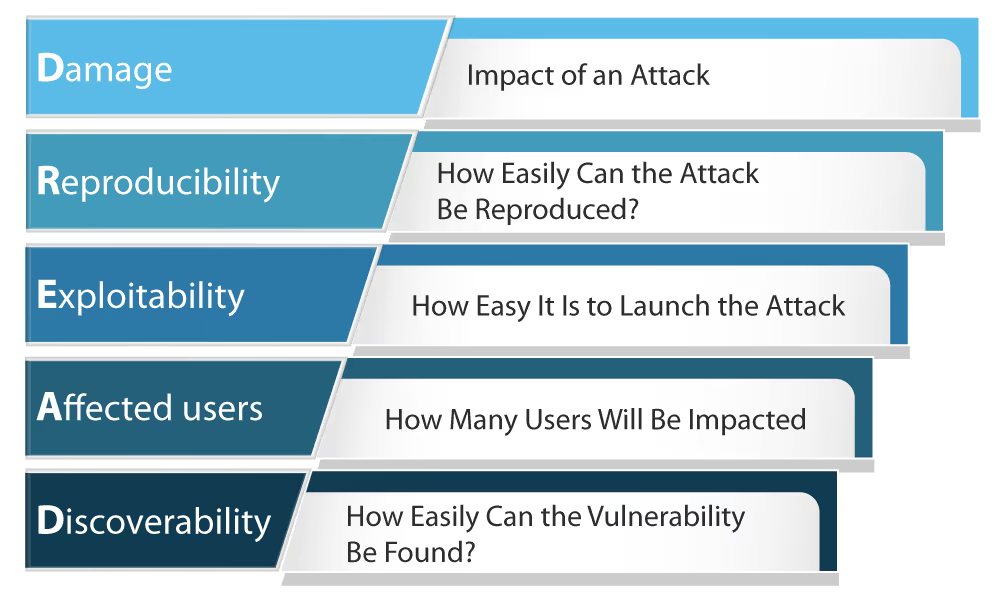
DREAD stands for Damage, Reproducibility, Exploitability, Affected Users, and Discoverability.
- Damage refers to the potential impact that a vulnerability could have on the target, which can be the organization, the system in question, or other users in general.
- Reproducibility: Refers to how easily an attacker can reproduce the vulnerability.
- Exploitability: Refers to how easy or difficult it is to exploit the vulnerability.
- Affected Users: Refers to the number of users affected by the vulnerability.
- Discoverability: Refers to how easy or difficult it is to discover the vulnerability.
The DREAD model can be compared to the Common Vulnerability Scoring System (CVSS) in its methodology for assessing the severity of identified threats. Software Secured employs a blended approach utilizing both DREAD and CVSS in the evaluation of vulnerabilities.
The DREAD framework can assess the severity of individual threats that have already been identified using other methodologies, such as STRIDE. Once a threat has been identified, DREAD helps measure its potential severity by assigning scores.
Its methodology can provide a quick and effective way to identify and prioritize potential threats and allows organizations to focus on the most critical threats first.
However, the DREAD framework also has some limitations. One limitation is that it is focused solely on technical threats and does not consider other factors that could impact the severity of a potential threat, such as its impact on business operations or reputation.
Additionally, the framework may not provide sufficient detail to assess the severity of a potential threat fully, and the scores assigned to each category may be subjective and vary based on individual perspectives.
The PASTA Framework
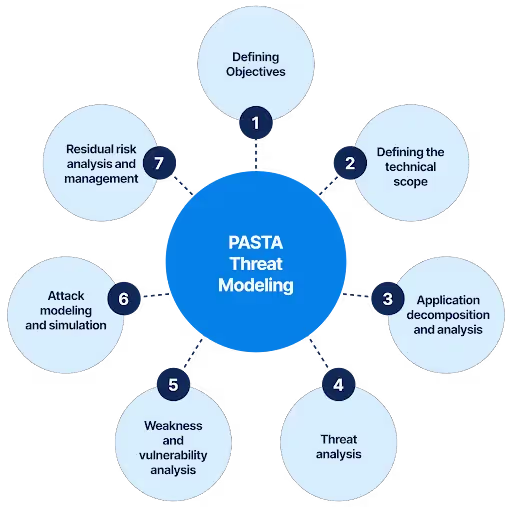
PASTA stands for Process for Attack Simulation and Threat Analysis. It is a seven-step methodology for identifying, analyzing, and prioritizing threats and attacks in software applications. The PASTA framework is comprehensive and focuses on a risk-based approach to threat modelling.
The PASTA methodology follows a seven-step approach for threat modelling:
- Define Objectives: Identify the security objectives and goals of the system being modelled.
- Define Technical Scope: Define the technical scope of the system and its boundaries.
- Decomposition and Analysis: Decompose the system into smaller components and analyze each of them for potential threats.
- Threat Analysis: Identify and prioritize the potential threats and their attack vectors.
- Vulnerabilities and Weaknesses Analysis: Identify and analyze potential vulnerabilities and weaknesses in the system.
- Modeling and Simulation: Create a visual model using diagrams and simulations to assess the system's security posture.
- Risk Impact Analysis: Evaluate the risks associated with identified threats and vulnerabilities and prioritize them for risk mitigation.
PASTA is often used in organizations with a mature security program. It can guide the development of countermeasures to address the identified risks. This framework is flexible, allowing organizations to customize the methodology to meet their specific needs.
PASTA requires a high level of expertise to implement correctly and is typically very time-consuming. It is also a complex methodology that may not be suitable for smaller organizations with limited resources. Additionally, PASTA does not provide specific guidance on addressing the identified risks, so additional expertise may be required to develop an effective risk mitigation plan.
Now that we have explored the STRIDE, DREAD, and PASTA threat modelling frameworks, you may wonder which best suits your organization. Let’s discuss some key factors to consider when choosing a threat modelling framework to help you make an informed decision.
When to Use Each Threat Modeling Framework
Each threat modelling framework discussed above has unique features and is best suited for certain types of organizations. The decision of which one to use ultimately depends on your specific needs and goals, such as business goals, the complexity of your system, and available resources. Let’s look into which threat modelling framework is right for you based on the type of organization.
STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege):
- When to Use
- Use STRIDE during the design phase of development to identify specific threat categories for system components.
- Best for software or application security projects where a detailed breakdown of potential threats is needed.
- Suitable for modeling threats against system architectures and helping design countermeasures early in the lifecycle.
- Key Advantage: Provides a structured framework for identifying threats tied to specific system properties (e.g., authentication, integrity).
DREAD (Damage, Reproducibility, Exploitability, Affected Users, Discoverability):
- When to Use:
- Use PASTA for complex, enterprise-level applications or systems where a comprehensive and contextual threat analysis is required.
- Ideal for aligning threat models with business objectives and operational impact.
- Suitable for advanced scenarios requiring attack simulations to predict potential threat scenarios and inform strategic decisions.
- Key Advantage: Combines technical and business perspectives, making it useful for organizations with critical operations or compliance requirements.
PASTA (Process for Attack Simulation and Threat Analysis):
- When to Use
- Use PASTA for complex, enterprise-level applications or systems where a comprehensive and contextual threat analysis is required.
- Ideal for aligning threat models with business objectives and operational impact.
- Suitable for advanced scenarios requiring attack simulations to predict potential threat scenarios and inform strategic decisions.
- Key Advantage: Combines technical and business perspectives, making it useful for organizations with critical operations or compliance requirements.
Should You Hire Professionals?
Performing Threat Modelling could be a daunting task. Consider using professionals in the following cases
1. Complex Systems:
- When the system or application is highly complex, involving multiple interconnected components, third-party integrations, or critical infrastructure.
- Professionals bring experience and tools to handle intricate threat modelling effectively.
2. Lack of In-House Expertise:
- If your team lacks experience with structured threat modelling frameworks (e.g., STRIDE, PASTA) or tools.
- Professionals ensure thorough analysis without gaps caused by inexperience.
3. Compliance and Regulatory Requirements:
- Professionals can provide specialized knowledge to meet regulatory needs for systems that must comply with strict standards (e.g., PCI-DSS, GDPR, HIPAA).
4. Critical Applications or High Stakes:
- A thorough and expert-driven approach minimizes risk for systems handling sensitive data, financial transactions, or mission-critical operations.
5. Limited Resources:
- Outsourcing ensures timely and accurate results when your team lacks the time or bandwidth to conduct a detailed threat model.
In today’s digital landscape, prioritizing the most critical risk is the most time-consuming task, according to a survey done by Hyperproof with 1000 security professionals. Whether you’re managing complex infrastructure, safeguarding sensitive data, or navigating regulatory requirements, professional threat modelling can be the difference between a secure system and a costly vulnerability.

At Software Secured, we bring years of expertise to professionally implement threat modelling for your application, system, or network. Our team works with you to align security strategies with your business goals, delivering tailored solutions that protect your operations and instill confidence in your stakeholders.
About Software Secured:
Software Secured offers high-quality manual penetration testing combined with our proprietary testing stack to provide a more comprehensive test. Streamline multiple security projects in one place through Portal, the online reporting dashboard that allows you to manage tests, track SLAs, download reports, and view your security posture over time.
Software Secured offers baseline penetration testing for one-time proof of your application security or year-round security coverage through Penetration Testing as a Service (PTaaS). Software Secured also offers a variety of augmented services such as security code review, internal network pentesting, secure cloud review and threat modelling.
If you are interested in learning more or booking a threat modelling service, please book a call with us.

.avif)



