Crowdsourced Pentesters vs. Full-Time Pentesters: Which Is Right for Your Security Strategy?
Penetration testing helps organizations identify vulnerabilities in their systems before malicious actors can exploit them. When it comes to conducting penetration testing, organizations have two primary vendor options: crowdsourced pentesters or full-time pentesters.
Penetration testing helps organizations identify vulnerabilities in their systems before malicious actors can exploit them. When it comes to conducting penetration testing, organizations have two primary vendor options: crowdsourced pentesters or full-time pentesters. Each approach has its unique advantages and challenges, and the right choice depends on your organization’s needs, budget, and goals.
What Are Crowdsourced Pentesters?
Crowdsourced pentesters are external cybersecurity professionals who participate in bug bounty programs or are contracted by pentesting firms to identify and report vulnerabilities. Platforms such as Bugcrowd, HackerOne, and Synack connect organizations with a global pool of skilled testers who bring diverse expertise to the table.
Organizations typically post challenges or bug bounty programs outlining the scope of testing. These testers compete to discover vulnerabilities, often operating on a pay-for-results model. This approach provides on-demand scalability and access to a wide range of skills, making it a flexible option for organizations with specific or occasional testing needs.
What Are Full-Time Pentesters?
In contrast, full-time pentesters are cybersecurity experts employed directly by an organization. Their role is to conduct ongoing penetration testing, perform regular vulnerability assessments, and collaborate with internal teams to enhance the organization’s security posture.
Full-time pentesters have a deeper understanding of the organization’s business logic, systems, applications, and security requirements. They are integrated into internal processes and are consistently engaged in improving the organization’s security infrastructure and program. This approach is well-suited for organizations that require continuous security testing and alignment with long-term business objectives.
Key Differences Between Crowdsourced and Full-Time Pentesters
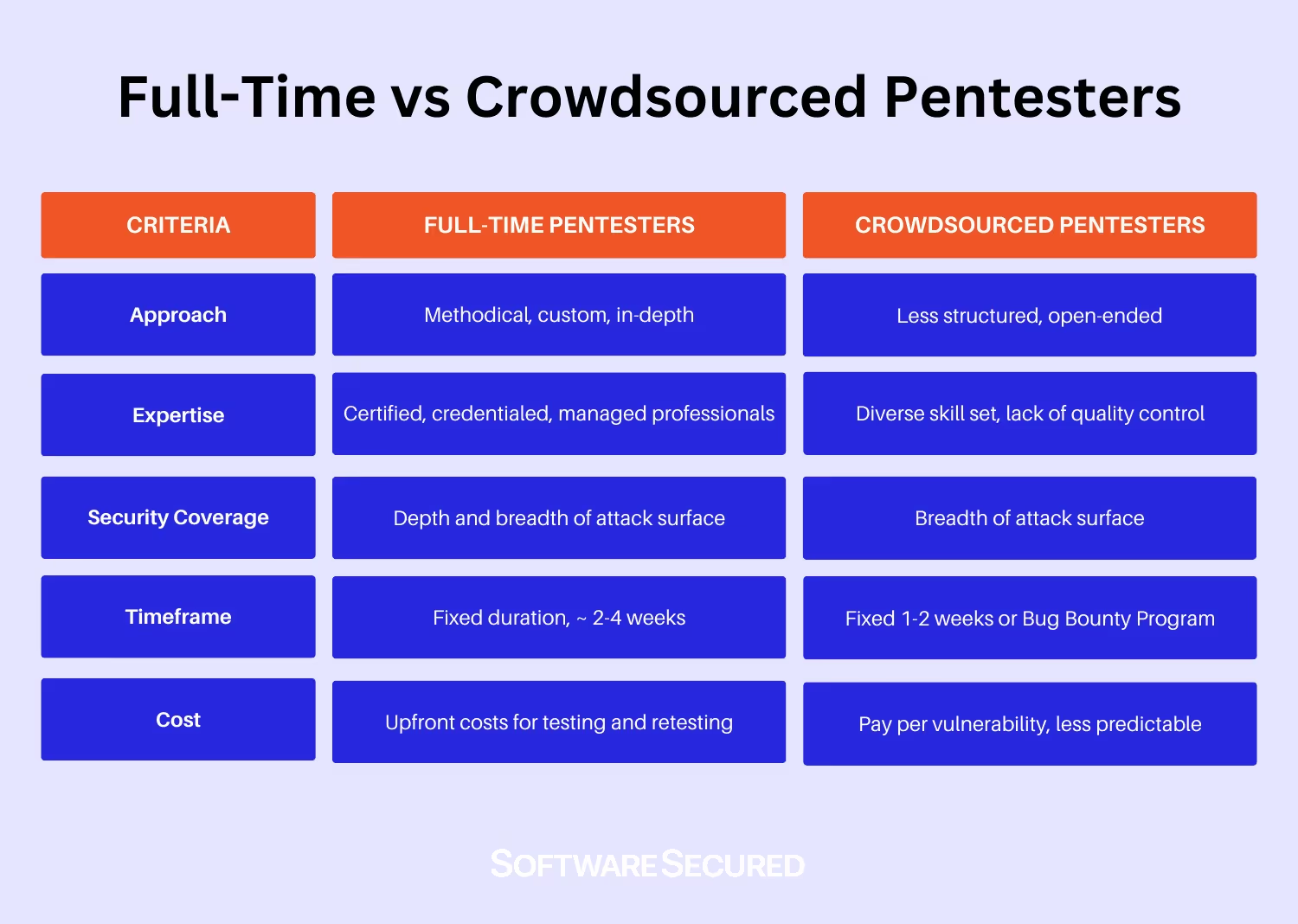
- Workforce Scope: Crowdsourced pentesting vendors draw from a global pool of testers with varied expertise, while full-time pentesters are dedicated to your organization and have a deep understanding of internal systems.
- Engagement Model: Crowdsourced pentesters are typically project or program-based, ideal for specific or short-term needs. Full-time pentesters provide ongoing and consistent involvement in security initiatives.
- Cost Structure: Crowdsourced programs operate on a pay-for-results basis, often making them cost-effective for one-off projects. Full-time teams are committed to continuous assessments and are salaried employees. The cost for organizations depends on the size of their attack surface, creating a different incentive structure.
- Specialization: Crowdsourced testers offer varying skills and perspectives, while full-time teams specialize in your organization’s specific environment and business logic.
- Flexibility: Full-time penetration testers provide the flexibility to thoroughly understand the attack surface and offer detailed guidance on mitigation options when risk elimination isn't feasible. In contrast, crowd-sourced testers typically lack the time to develop a deep understanding of the attack surface and risk profile.
Full-Time vs Crowdsourced Pentesters
Pros and Cons of Crowdsourced Pentesters
- Pros:
- Access to a wide range of skills and expertise.
- Cost-effective for targeted testing needs.
- Scalable for urgent or large-scale projects.
- Global talent that can adhere to regional data privacy laws.
- Cons:
- Limited understanding of organizational systems and culture.
- Potential inconsistency in the quality of findings.
- Dependence on external platforms for collaboration.
- Risks associated with sharing sensitive data with external parties
Crowdsourced penetration testing, while offering diverse perspectives, faces significant challenges in maintaining consistency and standardization across the security testing process. The varying levels of expertise, methodologies, and thoroughness among individual testers can lead to substantial discrepancies in vulnerability identification and reporting. This inconsistency may result in critical security gaps being overlooked or inadequately addressed. Furthermore, the lack of a unified approach can make it difficult for organizations to compare results across different tests or establish a reliable baseline for their security posture. The absence of standardized procedures and reporting formats can also complicate the process of prioritizing and addressing identified vulnerabilities, potentially leaving organizations exposed to undetected risks. Penetration testing is an invasive process that is required at least annually. While crowd-sourced pentesters can often begin testing right away, this approach may result in a poor-quality experience and subpar outcomes in the long run. These testers often lack the incentive to fully understand your organization’s needs beyond simply checking a box for compliance.
Pros and Cons of Full-Time Pentesters
- Pros:
- Deep understanding of the organization’s systems and processes.
- Consistent, ongoing security improvements.
- Strong alignment with business objectives.
- Greater control over sensitive data.
- Cons:
- Potential localized nuanced security and privacy knowledge based on geography.
- Capacity constraints during periods of high demand.
Full-time penetration testers are compensated for identifying meaningful security risks and effectively reporting and communicating those risks to your team or clients in an actionable manner. Their goal is to build long-term relationships as representatives of your company, unlike crowd-sourced testers. This approach can significantly enhance the customer experience and improve how stakeholders perceive and utilize your penetration test report.
How to Decide if Crowdsourced or Full-Time Pentesters Are Best for Your Organization
When deciding between crowdsourced and full-time pentesters, consider the following factors:
- Assess Your Security Needs: Evaluate how often testing is required, the complexity of your systems, and the sensitivity of your data. Crowdsourced testers may be better suited for occasional or highly specialized testing, while full-time teams excel in ongoing security improvement whether it's annual, quarterly or monthly testing that your clients and security program require.
- Budget Considerations: Compare the costs of each approach. Crowdsourced testing offers a pay-for-results model, which can be more economical for one-off projects, but may not be comprehensive when it comes to assessing your overall attack surface for risk. Full-time teams require fixed costs but provide continuous value.
- Long-Term Security Goals: Consider whether your organization needs continuous testing and improvement or can manage with ad-hoc assessments. Organizations aiming to build internal security expertise and culture may benefit from an full-time team.
When deciding between crowdsourced and full-time penetration testers, it’s essential to consider how each aligns with your organization’s security needs, long-term goals, and budget. Crowdsourced testers may be a good fit for one-off testing that can be cost-effective for organizations but often lacks the depth and continuity needed to address complex attack surfaces or build a comprehensive security strategy. Full-time pentesters, on the other hand, provide ongoing value by embedding themselves into your security program, continuously improving your defences, and offering actionable insights tailored to your organization’s unique risk profile. While they require a fixed investment, their ability to identify meaningful security risks, communicate them effectively to stakeholders, and align mitigation strategies with your business objectives makes them a strategic partner in strengthening long-term resilience. Choosing full-time pentesters reflects a commitment to proactive risk management and a culture of security, ensuring your organization is equipped to navigate an evolving threat landscape and meet the expectations of clients and regulatory requirements.
Conclusion
Both crowdsourced and full-time pentesters offer unique benefits and challenges. The best choice for your organization depends on your specific goals, security requirements, and budget. Regardless of the approach, it is essential to regularly review and adapt your cybersecurity strategy to address evolving threats effectively.
Take the first step toward strengthening your security posture by evaluating your current approach and determine whether crowdsourced pentesters, full-time teams, or a hybrid model fits your needs. Explore our resources or schedule a consultation to find the best pentesting strategy for your organization.




