Why Developer Security Awareness is More Than Just OWASP Top 10
OWASP Top 10 is not enough. Read this post to learn what more developers need to know.
The world is increasingly embracing digital technology, and hackers are doing the same. Cyber attacks have become common. As businesses expand their online presence, the likelihood of attracting a cyber attack increases. External penetration testing can serve as your protective shield if you want to protect your company from potential harm.
External network penetration testing is a type of security assessment that focuses on identifying and exploiting vulnerabilities in an organization's externally facing systems and infrastructure, such as websites, email servers, firewalls, and other publicly accessible assets. The goal is to simulate an attack from the perspective of an external adversary who does not have internal access to the organization's network.
Vulnerability scanning is an automated process that identifies security weaknesses or vulnerabilities in an organization's systems, networks, applications, or devices. It uses specialized tools to scan for known vulnerabilities, misconfigurations, outdated software, and other potential security issues, providing a detailed report to help organizations address these risks.
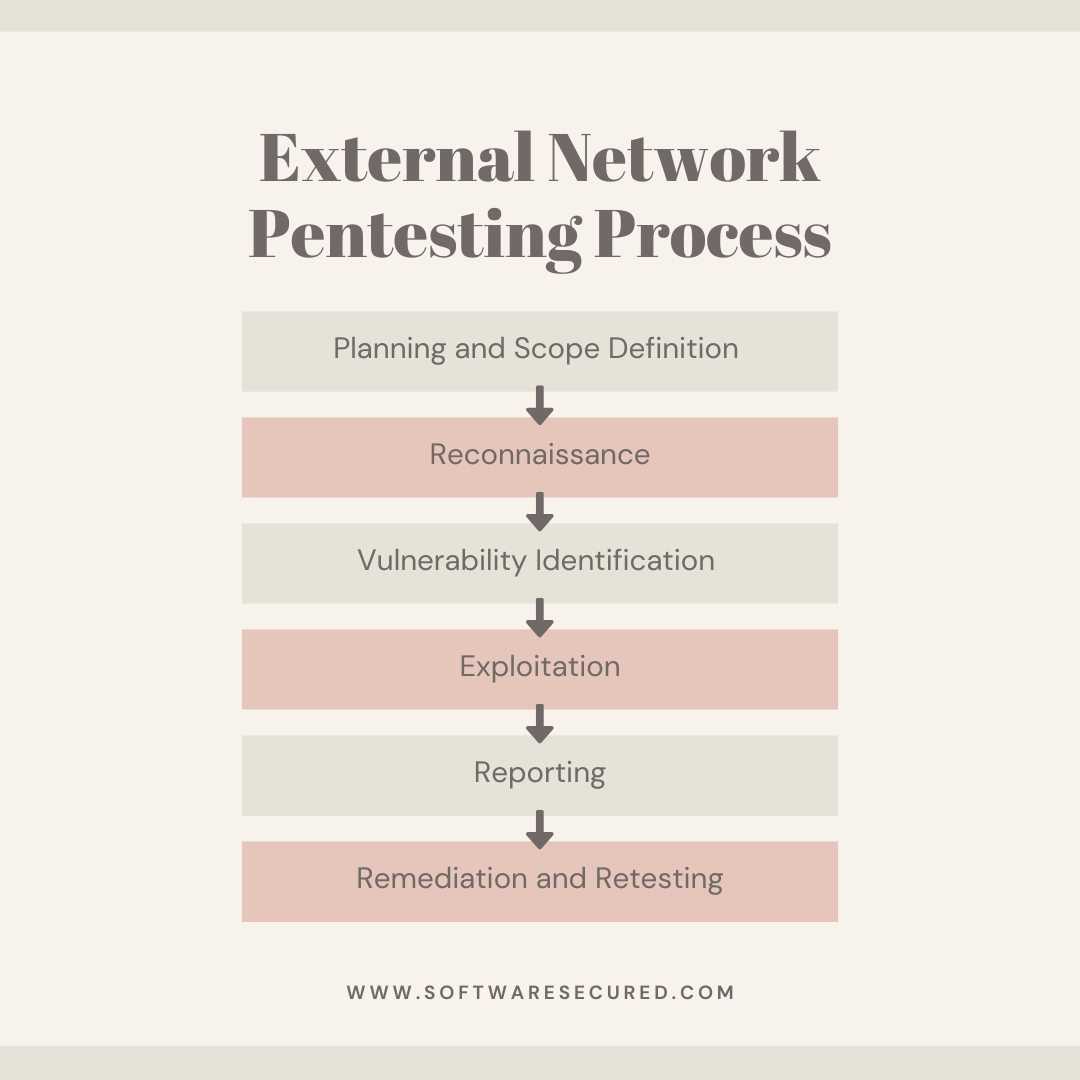
Conducting an external penetration test involves several key steps:
The cost varies based on factors like the scope of testing, the complexity of your systems, and the expertise required. While an investment is involved, the cost of a breach can be far greater. Investing in penetration testing can save you significant time and money in the long run.
Software Secured's External Network Pentest starts from $5,400, check our prices.
Take the Next Step—don't leave your security to chance. Contact us today to learn how Software Secured can tailor an external penetration testing solution to meet your specific needs. Together, we'll build a robust defence that keeps your business and customers safe.
.jpg)
Sherif Koussa is a cybersecurity expert and entrepreneur with a rich software building and breaking background. In 2006, he founded the OWASP Ottawa Chapter, contributed to WebGoat and OWASP Cheat Sheets, and helped launch SANS/GIAC exams. Today, as CEO of Software Secured, he helps hundreds of SaaS companies continuously ship secure code.
Security
Can be easily manipulated without detection if not properly secured.
Digitally signed and can be validated on the server. Manipulation can be detected.
Size
Limited to 4KB.
Can contain much more data, up to 8KB.
Dependency
Often used for session data on the server-side. The server needs to store the session map.
Contains all the necessary information in the token. Doesn’t need to store data on the server.
Storage Location
Browser cookie jar.
Local storage or client-side cookie.
Securing healthcare systems isn’t about buying one flashy tool—it’s about building a hardened stack, layer by layer. Healthcare organizations deal with exposed APIs, legacy systems, undersecured medical devices, and sensitive patient data that hackers actively target. A generic setup won’t cut it.


Providing the quality of the biggest names in security without the price tag and complications.
Manual penetration testing
Full time Canadian hackers
Remediation support
