Best Healthcare Cybersecurity Companies: Build a Proven Security Stack
Compare top healthcare cybersecurity companies and learn how to assemble a stack that protects patient data, supports HIPAA/HITRUST compliance, and accelerates enterprise readiness
Each layer, identity, endpoint, cloud, application, network, compliance, needs its own specialized solution. You need tools that do one job and do it right: control access, spot intrusions fast, block lateral movement, detect misconfigurations, and prove compliance without the hand-waving.
This guide breaks down the essential components of a serious healthcare security stack. We’ve mapped each category to tools picked for their technical depth, HIPAA and HITRUST alignment, and real-world performance. Whether you're locking down a healthtech startup or tightening an existing setup, this is the stack you build if you’re serious about stopping breaches and passing audits.
Why Listen to Us
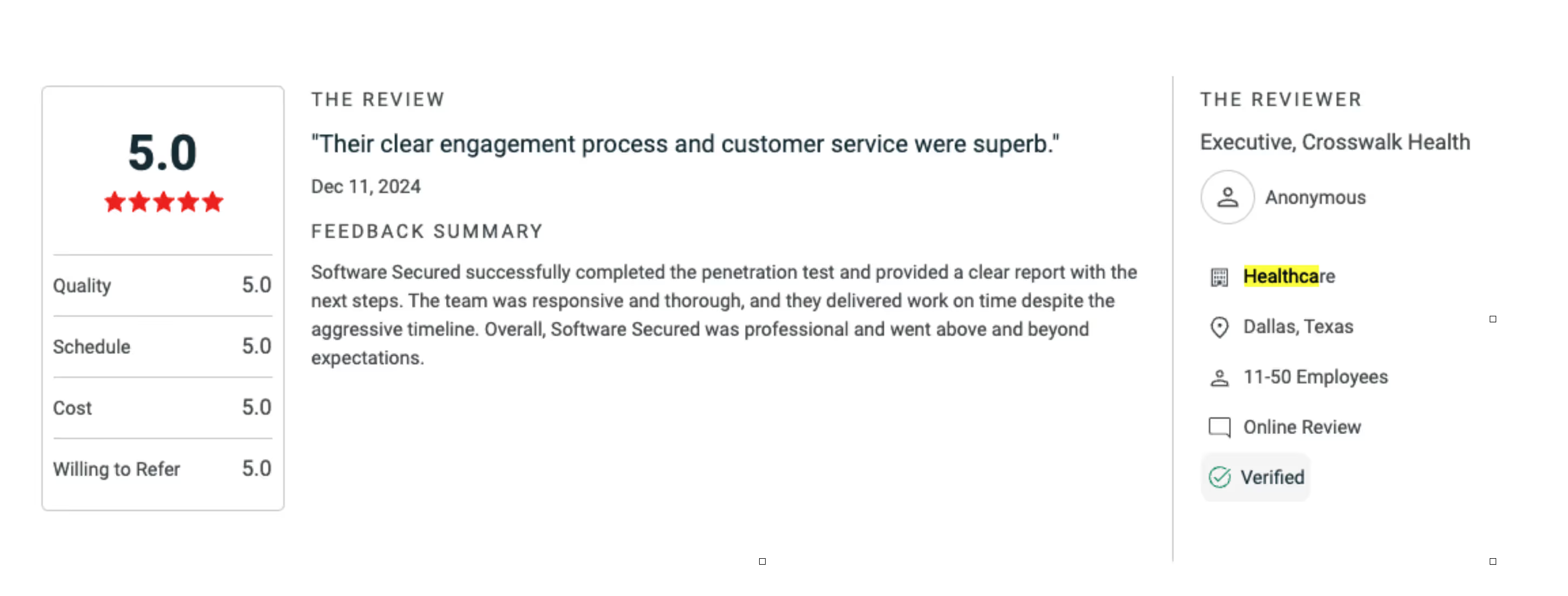
At Software Secured, we manually hack healthcare apps for a living. Our team works with fast-moving healthtech companies to uncover real risks, not checkbox findings. One client put it best: “Software Secured successfully completed the penetration test and provided a clear report with the next steps. The team was responsive and thorough, and they delivered work on time despite the aggressive timeline. Overall, Software Secured was professional and went above and beyond expectations.”
Why Healthcare Needs a Strategic Security Stack Approach
A piecemeal approach to healthcare security doesn’t work. Buying one tool for each audit gap leads to a fragmented mess, overlapping features, blind spots, and wasted spend. Worse, it gives a false sense of protection. Real security comes from a coordinated, layered stack designed to stop real attacks.
According to the Medical Group Management Association: “If you are relying on a single layer, you are asking for trouble”
The following is a presentation from BlackHat was given in 2021. The core of this presentation focus on vulnerabilities and design issues within healthcare solutions. This demonstrates inherit pobnumerous clinical focused systems, including radiology reading, EMR downtime, patient entertainment, pharmacy distribution, nurse communication, M&A EMR, clinical documentation and temperature monitoring systems, the prognosis doesn’t look good. Unfortunately, it is our experience that there are few solutions within the hospital enterprise that do not have issues.
Why one layer isn't enough
If you're relying on a single security tool, you're asking for trouble. No one tool can stop every attack; layered security gives you multiple opportunities to catch a threat before it causes damage.
Beyond Compliance Checklists – Real protection requires layered security
Passing HIPAA or HITRUST doesn’t mean you’re safe. Attackers don’t care about your compliance badges, they look for weak access controls, outdated endpoints, and unpatched web apps. You need overlapping defenses that catch what others miss.
Integration Matters – Tools must work together, not create silos
Security tools that don’t talk to each other leave gaps. Alerts get buried, coverage overlaps, and teams waste time. The right stack shares context, so your EDR knows what your firewall sees, and your pentest findings feed into your SIEM.
Healthcare-Specific Threats – Generic solutions miss industry nuances
Connected devices, patient portals, EHR integrations, these aren’t covered by off-the-shelf tools. You need solutions built for the way healthcare actually works.
The Essential Healthcare Cybersecurity Stack
Healthcare security isn’t a grab-bag of tools, a carefully architected stack. Each layer must solve a specific risk vector, feed context into the next, and serve healthcare’s strict HIPAA/HITRUST audit demands. Below is a tight stack of tools built for healthcare: from pentesting to vulnerability management to EDR, identity, network, and SIEM/SOAR, vendors chosen for real-world coverage, integration capability, and compliance focus.
Detailed Stack Component Reviews
1. Penetration Testing
Penetration testing is the most direct way to identify potential vulnerabilities that attackers could exploit. For healthcare organizations, it’s not just a best practice, mandated by HIPAA and expected in HITRUST assessments. But not all pentests are equal. In healthcare, testing must go beyond surface-level scans to simulate real attacks against APIs, cloud infrastructure, EHRs, and connected devices.
Software Secured: Best for Healthcare Penetration Testing

Software Secured specializes in high-assurance, manual penetration testing with a strong track record in healthcare, thanks to their test plan targeted specifically towards Healthcare applications Unlike PTaaS vendors that automate or crowdsource, Software Secured pairs each client with a dedicated offensive security team that works closely with internal developers and compliance leads.
With deep experience in HIPAA, HITRUST, SOC 2, and ISO 27001 environments, the company goes beyond basic vulnerability discovery to help teams understand root causes, prioritize remediation, and align fixes with real business risk. For fast-moving healthtech startups and mid-sized providers, Software Secured helps avoid false positives, wasted cycles, and audit pain.
Key Services
- Manual App & API Pentesting: Senior testers map abuse paths across roles, workflows, and PHI flows to surface real impact and prioritized fixes.
- Dedicated test plan for healthcare applications: Deeper testing of patient portals, EHR integrations, and web apps, including authenticated paths and business logic flaws.
- Secure Code Review: Deep dives on high-risk components with annotated findings, code-level guidance, and diffs to validate fixes.
- Infrastructure Penetration Testing: Tests cloud and on-prem environments for lateral movement, privilege escalation, misconfigurations, and more.
- Retesting & Verification: Includes three rounds of remediation verification to ensure fixes are implemented correctly and hold up.
- Secure Portal & Dashboards: Access detailed findings, retest status, and evidence through a secure, compliance-friendly dashboard.
- Threat Modeling Support (Optional): Helps organizations understand what matters most before testing even begins.
Pricing
Pricing is scoped based on attack surface size, complexity, and frequency, delivered as a project or subscription model. However, external network pentests start from $5400, and authenticated web application pentests from $10k.
Pros
- Deep manual testing, no crowdsourcing, and mature methodology
- Strong healthcare footprint and references.
- Strong communication and support for the developer handoff
- Excellent for scaling SaaS healthcare startups
- Slack support and SDLC integration
Cons
- Not a fit for companies looking for ultra-cheap automated scans
- Turnaround may be slower than PTaaS tools in burst-mode engagement.
Best Suited For
Ideal for digital health startups and SMBs that need deep coverage, compliance-aligned results, and support beyond just finding issues. Also works well for orgs prepping for HITRUST or enterprise due diligence.
Cobalt.io: Best for Platform-Based Pentesting
Key Services
- PTaaS Web & API Testing: Fixed-scope starter packages with live findings and Jira/GitHub/Azure DevOps integrations to move evidence fast.
- Compliance Reporting & Attestations: Audit-friendly reports and downloadable letters suited for HIPAA evidence.
- Fast Kickoff & Fix Validation: Start in as little as 24 hours/≈5 business days; validation included in starter package.
- Vetted Tester Community: The Cobalt Core provides experienced freelance pentesters for coverage and speed.
Pricing
Public starter packages: Small $8,500, Medium $13,600, Large $20,400; larger programs use a credit model.
Pros
- Quick spin-up and strong integrations.
- Transparent entry pricing.
- OWASP-aligned methodology.
- Attestations for audits.
Cons
- Community delivery may not fit teams needing a dedicated vendor.
- Fixed package scopes can feel tight for complex apps.
Best Suited For
Healthcare startups and digital-health vendors needing fast, budgetable web/API/LLM tests with audit-ready outputs and ticket-driven remediation
NetSPI: Best for Enterprise Penetration Testing
Key Services
- PTaaS with in-house experts: 300+ employed pentesters, real-time findings, consistent delivery.
- App, API, Cloud, Network PT: Enterprise-depth testing across web/mobile/APIs and AWS/Azure/GCP.
- Hardware/Embedded & IoT: Coverage that includes medical devices and other cyber-physical systems.
- Workflow Integrations: Open API and 1,000+ connectors (e.g., Jira/ServiceNow) to speed remediation.
Pricing
Quote-based; no public list pricing. AWS Marketplace lists contract-driven terms and private offers.
Pros
- Employed (not freelance) testing team with scale.
- Mature testing capability.
- Strong healthcare footprint and references.
- Robust integrations and remediation flow.
Cons
- Pricing lacks public transparency (contract/PO-driven).
- Program-heavy approach may be more than very small teams need.
Best Suited For
Mid-market to enterprise healthcare providers, payers, and digital-health platforms that want PTaaS with named in-house testers, LLM coverage, and tight integration into ticketing and release workflows.
2. Identity & Access Management
Identity & Access Management (IAM) ensures the right clinicians, staff, vendors, and workloads get the right access to the right systems, only when they need it. By combining SSO, phishing-resistant MFA, automated provisioning, and just-in-time privileged access, IAM enforces least privilege across EHRs, cloud apps, and medical devices. For healthcare, strong IAM protects PHI, reduces account-takeover and ransomware risk, and preserves clinical workflows (e.g., fast, secure access during shifts and emergencies). It also provides the audit trails and policy controls needed to demonstrate HIPAA compliance and satisfy security reviews from partners and regulators.
Microsoft Entra ID (P1/P2): Best for Native Enterprise Identity & Access Management
Key Services:
- Enterprise-Grade IdP: Centralized identity platform with seamless integration into Microsoft 365, Azure, and thousands of third-party apps.
- Conditional Access: Enforces access policies based on user, device, location, and risk signals.
- Identity Protection: Risk-based detection and automated remediation of compromised accounts (P2).
- Privileged Identity Management (PIM): Just-in-time admin access with approval workflows and activity logging (P2).
- Passwordless Authentication: Supports passkeys, FIDO2 security keys, and Microsoft Authenticator for strong MFA.
- Compliance Coverage: HIPAA BAA included under Microsoft’s Online Services Terms, plus broad regulatory alignment.
Pricing:
Licensed per user; Microsoft publishes public pricing. P1 includes Conditional Access and basic governance; P2 adds Identity Protection and PIM.
Pros:
- Deep integration with Defender, Intune, and Azure AD ecosystem.
- Strong governance and compliance posture out of the box.
- Robust passwordless and MFA support.
Cons:
- Full feature set often requires P2 licensing.
- Best value when already in Microsoft ecosystem.
Best Suited For:
Organizations already using Microsoft 365 or Azure that want turnkey identity management, advanced security controls, and tight integration with Microsoft’s security stack.
Okta Workforce Identity Cloud: Best for Vendor-Neutral, Best-of-Breed IAM

Okta Workforce Identity Cloud delivers a flexible, vendor-neutral identity platform ideal for healthcare organizations operating across mixed technology stacks. It provides secure single sign-on (SSO), adaptive MFA, and advanced lifecycle automation, backed by one of the industry’s largest application integration catalogs.
Key Services:
- Single Sign-On (SSO): Centralized access to thousands of apps through the Okta Integration Network (OIN).
- Adaptive MFA: Risk-based authentication with phishing-resistant methods like FastPass and FIDO2.
- Lifecycle Management: Automated provisioning/deprovisioning via SCIM with deep directory integrations.
- No-Code Workflows: Visual automation for onboarding, offboarding, and compliance processes.
- HIPAA-Regulated Cell: Dedicated environment for in-scope services with signed BAA.
- Cross-Stack Support: Seamless integration across AWS, GCP, and multi-SaaS environments.
Pricing:
Per-user suite licensing (Starter, Essentials, Pro, Enterprise), with Workflows and Lifecycle features scaling by tier; HIPAA cell pricing is custom.
Pros:
- Massive integration library
- Strong MFA options, including phishing-resistant methods
- Scalable lifecycle automation
Cons:
- Advanced features require higher-tier licenses
- HIPAA cell only available on request
Best Suited For:
Healthcare providers and digital health platforms needing flexible IAM for diverse environments and HIPAA-aligned identity solutions.
3. Endpoint Security (EDR/XDR)
Endpoint security (EDR/XDR) is critical because endpoints, clinician laptops, shared workstations, and connected devices, are the easiest path to PHI and the fastest way attackers move laterally. EDR/XDR provide continuous telemetry and behavior-based detection to catch credential theft, ransomware staging, and data exfiltration in real time. They also automate containment (isolate a host, kill a process, roll back changes) to shrink blast radius and downtime for clinical apps. Finally, the alerting and audit trails help meet HIPAA expectations for incident detection, response, and reporting.
CrowdStrike Falcon: Best for Advanced Threat Protection in Healthcare
CrowdStrike Falcon is a cloud-native endpoint detection and response (EDR/XDR) platform designed for high-accuracy threat prevention, detection, and hunting across clinical workstations, shared endpoints, and IoT/IoMT devices. Its single lightweight agent captures telemetry from endpoint, identity, and cloud activity, correlating signals to detect ransomware, credential theft, and stealthy lateral movement.
Key Services:
- Falcon Insight XDR: Unified telemetry with real-time threat detection and response.
- Falcon Complete (MDR): Fully managed 24/7 detection, investigation, and remediation.
- Adversary OverWatch: Proactive human-led threat hunting to catch advanced attacks early.
- Identity Threat Protection: Stops credential abuse and privilege escalation in Active Directory and SSO.
- Healthcare Solution Pack: Tailored protection for clinical devices and medical IoT/IoMT fleets.
Pricing:
Quote-based per-endpoint subscription; bundles vary by modules included.
Pros:
- Strong cross-domain detection and lightweight agent
- 24/7 MDR option with full remediation
- Proven record in healthcare environments
Cons:
- Premium pricing compared to some EDRs
- Requires careful change control for updates
Best Suited For:
Healthcare organizations needing enterprise-grade endpoint visibility, proactive threat hunting, and MDR capabilities to protect critical clinical systems and patient data.
Microsoft Defender for Endpoint: Best for Integrated Healthcare Security Environments

Microsoft Defender for Endpoint (MDE) delivers enterprise-grade endpoint detection and response (EDR) tightly integrated with Microsoft 365 and Azure ecosystems. For healthcare organizations, it provides continuous telemetry, automated investigation, and real-time remediation to protect clinician workstations, shared devices, and medical IoT endpoints from ransomware, credential theft, and lateral movement.
Key Services:
- EDR with Automated Investigation & Response: Detects threats and triggers automated containment/remediation.
- Threat & Vulnerability Management: Prioritizes risks with guided mitigation steps.
- Attack Surface Reduction: Enforces exploit and ransomware blocking policies.
- Defender XDR Correlation: Links endpoint data with identity, email, and cloud events for complete incident context.
- Microsoft Sentinel Integration: Streams alerts for SIEM analysis, compliance, and playbook automation.
Pricing:
Available as part of Microsoft 365 E5 or as a standalone license; feature set varies by plan.
Pros:
- Deep integration with Entra ID, Intune, and Sentinel
- Automated, cross-domain threat response
- Broad OS and device coverage
Cons:
- Complex licensing/prerequisites
- Top-tier features locked to higher plans
Best Suited For:
Healthcare organizations standardized on Microsoft 365 that want unified endpoint, identity, and email security with minimal vendor sprawl.
4. Network Security (NGFW + IDS/IPS)
Network Security for healthcare pairs next-generation firewalls (NGFW) with IDS/IPS to control traffic from Layer 3–7, decrypt and inspect TLS, and block known exploits as well as suspicious behaviors. In hospitals and healthtech environments, these controls segment EHR/PACS, clinical, admin, and guest networks; quarantine unmanaged medical/IoT devices; and enforce secure remote access. The result is a smaller blast radius for phishing-led intrusions and ransomware, prevention of PHI exfiltration, and earlier detection of lateral movement in otherwise flat or legacy networks. Detailed logging and policy baselines also support HIPAA risk management and partner security reviews without slowing clinical workflows.
Palo Alto Networks PA-Series: Best for Network-Level Healthcare Security

Palo Alto’s PA-Series firewalls offer deep visibility, real-time threat blocking, and zero-trust enforcement across complex healthcare networks. Unlike legacy firewalls, the PA-Series uses machine learning to stop unknown threats inline and inspects traffic based on application and user, not just IP or port.
Key Strengths
- Application- and user-aware filtering (App-ID, User-ID)
- Inline ML threat prevention with zero cloud delay
- IoT/medical device profiling and segmentation
- Scales from clinics to enterprise data centers
- Centralized rule management with Panorama
Pricing
Quote-based; ranges from ~$1K for entry models to $200K+ for enterprise chassis.
Pros
- Strong protection against evasive, encrypted threats
- Native medical device security
- Works across hybrid and on-prem setups
Cons
- High cost of ownership
- Complex setup may require specialized staff
Best Suited For
Hospitals and multi-site healthcare organizations that need full visibility, strict control, and enterprise-grade enforcement at the network edge.
Fortinet FortiGate (with FortiGuard UTP/IPS): Powerhouse for Healthcare Network Security
FortiGate puts a high-performance next-gen firewall at your perimeter and branches, backed by FortiGuard AI‑powered protection bundles. Designed for real-world threats, this combo inspects everything from packet payloads to URLs, blocking attacks without slowing down clinical workflows.
Key Strengths
- Deep packet inspection with virtual patching using FortiGuard IPS, stopping zero-days in real time
- Unified Threat Protection (UTP) adds web filtering, anti-botnet, and DNS blocking to IPS and antivirus
- Enterprise bundle (ENT) brings IoT detection, DLP, CASB, and AI-based inline malware prevention for broad coverage
- ASIC‑powered throughput up to hundreds of Gbps, deployable from clinics to enterprise data centers
- Native integration with Fortinet Security Fabric, context shared across tools, no blind spots
Pricing
Subscription-based: base firewall hardware plus FortiCare support and UTP (or higher) bundles; firewall hardware for SMBs runs from ~$700–$4,000, UTP renewal ~$9,000–$12,000 over 3 years
Pros
- Real‑time defense across multiple threat vectors
- Scalable, high‑throughput hardware ideal for medical campuses
- Strong IoT device and DLP support out of the box
Cons
- Licensing complexity, multiple subscriptions required
- Requires skilled teams to deploy and tune policies effectively
Best Suited For
Healthcare networks from mid-sized clinics to large hospitals needing performance, rich protections, IoT-aware filtering, and a unified, high-assurance network defense.
5. Security Information & Event Management (SIEM) & SOAR
Security Information & Event Management (SIEM) centralizes and correlates logs from across your stack to detect threats, investigate timelines, and prove what happened. Security Orchestration, Automation & Response (SOAR) turns those detections into repeatable playbooks, automating triage, enrichment, and containment to cut mean time to respond. In healthcare, SIEM+SOAR unify signals from EHR/PACS, NGFW/EDR, IAM, and cloud services to catch ransomware, account takeover, and insider misuse without slowing clinical workflows. They also generate audit-ready evidence (retention, case management, access trails) that supports HIPAA risk management and partner security reviews.
Microsoft Sentinel: Cloud-Native SIEM & SOAR Built for Scale

Microsoft Sentinel fuses SIEM and SOAR in one cloud-native platform, ingesting logs, hunting threats, and automating responses across multicloud and on-prem systems. It uses AI, threat intel, and automation playbooks to cut analyst workload and expose what others miss.
Key Strengths
- Unified SIEM and SOAR with AI-powered detection, UEBA, case management, and TI, all in one interface
- Content Hub: prebuilt analytics, connectors, hunting queries, and response playbooks, so you launch without building from scratch.
- Automation via Logic Apps: trigger automatic remediation, ticketing, or containment across tools
Pricing
You pay per ingested GB (pay-as-you-go) or commit to daily capacity, a flat cost up to ~65% cheaper
Pros
- Scales with cloud infrastructure and merges detection with response
- Ships with healthcare‑friendly connectors (e.g., Azure, Entra, M365 logs)
- Reduces alert fatigue via AI and automation
Cons
- Cost rises with data volume unless carefully scoped and optimized
- Requires skilled engineers to build effective playbooks and tune alerts
Best Suited For
Cloud-first healthcare orgs with Azure footprints—like healthtech startups or mid-tier providers—who need threat visibility, compliance-ready logging, and automated incident playbooks in one scalable solution.
Sumo Logic Cloud SIEM + Cloud SOAR: Unified Threat Detection & Automated Response
Sumo Logic delivers a cloud-native SIEM paired with Cloud SOAR to give healthcare organizations rapid, scalable threat detection and response without on-premises overhead. The SIEM normalizes and correlates logs from EHR systems, medical IoT, cloud workloads, and traditional security tools, surfacing high-fidelity alerts via entity-based analytics. Prebuilt content packs map directly to HIPAA, HITRUST, and PCI DSS requirements, accelerating compliance readiness.
Key Services:
- Cloud-native SIEM with elastic scaling
- Entity-based detection to reduce false positives
- Prebuilt healthcare compliance rules and dashboards
- Cloud SOAR with drag-and-drop playbooks for automated remediation
- Native threat intelligence enrichment
- Flexible ingestion from hybrid and multi-cloud sources
Pricing:
Subscription-based, driven by daily ingest volume (SIEM) and automation usage (SOAR).
Pros:
- Integrated SIEM and SOAR for seamless workflows
- Compliance-ready out of the box
- Scales easily for hybrid environments
Cons:
- Ingest-based pricing can spike with large log volumes
Best Suited For:
Healthcare providers and digital health firms needing rapid deployment, automated incident response, and strong compliance alignment.
6. Vulnerability Management
Vulnerability Management is the continuous process of discovering assets, assessing them for CVEs and misconfigurations, prioritizing by real-world exploitability, and driving remediation through patches or configuration changes. In healthcare, it shrinks the attack surface that ransomware and account takeover use to reach EHRs and PHI, and helps mitigate risks on legacy systems and medical/IoT devices where patching can be tricky. Effective programs pair authenticated scanning with agents and cloud connectors, push fixes via ITSM/patch tools, and track coverage/MTTR. The resulting evidence supports HIPAA risk analysis/management and strengthens partner security reviews.
Qualys VMDR: Best for Comprehensive Vulnerability Management

Key Services:
- Continuous Vulnerability Scanning: Automatically identifies vulnerabilities across endpoints, servers, and cloud environments in real-time.
- Detection & Prioritization: Uses threat intelligence and asset context to rank vulnerabilities based on actual risk.
- Automated Patch Deployment: Integrates with patch management tools to remediate vulnerabilities faster.
- Asset Inventory: Maintains an up-to-date inventory of all IT assets, including shadow IT.
- Compliance Reporting: Generates audit-ready reports for SOC 2, ISO 27001, PCI DSS, and other frameworks.
- Cloud & Container Security: Extends coverage to modern environments including Kubernetes and serverless.
Pricing:
Subscription-based, quote upon request; scales based on number of assets.
Pros:
- Highly scalable for enterprises and SMBs alike.
- Strong asset discovery and classification.
- Risk-based prioritization reduces patching overload.
Cons:
- Interface can be complex for smaller teams.
- Requires tuning to reduce noise from low-risk findings.
Best Suited For:
Organizations needing a unified vulnerability management solution with real-time detection, automated response, and compliance capabilities—especially in hybrid or multi-cloud environments.
SafeBreach: Best for Continuous Exposure Validation via Breach & Attack Simulation
SafeBreach delivers a continuous breach-and-attack simulation (BAS) platform that safely runs thousands of real-world attack scenarios across your network and cloud environments. Purpose-built to uncover where your defenses fail, it offers both Validate (simulations of actual TTPs) and Propagate (attack-path validation), combining proactive testing with attack impact analysis to give security teams a clear, business-centric view of risk.
Key Services:
- Continuous BAS (Validate): Runs real attacker tactics at scale to assess defense effectiveness across the kill chain.
- Attack Path Validation (Propagate): Maps how an attacker might move laterally to critical systems—helping prioritize remediation.
- Insights & Global Risk Director: Translates simulation data into business-risk metrics, visualized via dashboards and exportable for SOC/SOAR workflows.
- Extensive Playbook: Continuously updated library of known attack methods crafted by SafeBreach Labs for broad, real-time coverage.
- Managed Option (“SafeBreach-as-a-Service”): Platform plus expert onboarding, custom attack plans, remediation guidance, and dashboarding.
Pricing:
Quote-based, varies by deployment size and scope—includes fully managed service tiers.
Pros:
- Scalable, continuous testing of real-world attack paths
- Prioritizes remediation based on actual business risk
- Safe for production environments
- Supports integration with SOC/SOAR tooling
Cons:
- No public pricing, requires custom quotes
- Needs tuning of scenarios to match your environment
Best Suited For:
Enterprises and healthcare providers that want proactive, data-driven validation of defense controls, especially useful for compliance, M&A due diligence, and aligning security investments with actual risk posture.
Why Software Secured Anchors Your Healthcare Security Stack
Software Secured provides the foundational validation layer that proves your controls actually work against real attackers. Our manual penetration testing pressure-tests the stack end-to-end: we verify NGFW segmentation and IDS/IPS policies stop lateral movement, confirm SIEM detections and SOAR playbooks trigger at the right moments, challenge IAM (MFA, Conditional Access, JIT/PIM) to prevent privileged misuse, and ensure vulnerability-management closes the risks that matter. Unlike scanners, our testers chain issues across apps, APIs, cloud, and medical/IoT networks to expose business-logic and workflow gaps that automation misses, precisely where PHI is most at risk. We integrate with development workflows and compliance programs: tickets in your backlog, targeted fix guidance, remediation retests, and artifacts mapped to HIPAA/HITRUST/SOC 2. The result is a measurable feedback loop, find, fix, and verify, that hardens defenses, shortens MTTR, and provides audit-ready evidence. In a stack full of automated tools, Software Secured supplies the human adversary perspective that keeps the whole system honest.
Conclusion
A well-architected healthcare security stack delivers more than compliance, it creates a layered, defense-in-depth posture that protects sensitive patient data, critical systems, and care delivery from evolving threats. By integrating the right tools across penetration testing, IAM, endpoint, network, SIEM/SOAR, and vulnerability management, organizations gain visibility, resilience, and faster incident response. The key is not just choosing best-in-class solutions, but ensuring they work together seamlessly. The first step is validating your current posture through thorough, manual penetration testing, identifying real-world risks before attackers do. From there, build and integrate your stack to align with both operational needs and regulatory requirements.
Book a free consultation to assess your healthcare security stack

.avif)



