Is Penetration Testing Necessary for SOC 2? A Comprehensive Guide for B2B Startups
Discover why penetration testing is highly recommended for SOC 2 compliance. Learn the differences between Type I and Type II audits, and how proactive security measures can accelerate B2B sales and strengthen your startup’s defenses.
Why SOC 2 Is Highly Recommended
SOC 2 compliance offers many benefits for B2B startups. It’s not merely a checkbox exercise; it is a strategic asset that strengthens your organization in several key ways:
Building Trust and Competitive Advantage
- Credibility with Clients:
A SOC 2 report is a testament to your commitment to security and data protection. It shows that you have been independently audited against rigorous standards. This builds credibility with potential clients who are increasingly focused on data security. - Sales Differentiation:
For many B2B startups, the SOC 2 report becomes a competitive differentiator. In sales conversations, a SOC 2 attestation can alleviate customer concerns quickly, paving the way for faster deal closures. - Market Differentiation:
In a crowded marketplace, a SOC 2 report signals to customers and partners that you adhere to best practices, setting you apart from competitors who might not have undergone such stringent evaluations.
Accelerating Sales Cycles
SOC 2 can significantly shorten the sales cycle by reducing the time spent on security questionnaires and lengthy vendor evaluations. Consider these points:
- Faster Onboarding:
With SOC 2, your security practices have already been vetted by a reputable third party. This can cut down due diligence time during vendor selection processes. - Client Confidence:
When potential customers see that you are SOC 2 compliant—and supplement that with recent pentest reports—they gain immediate trust in your organization. This can be the deciding factor in winning enterprise contracts. - Reduced Negotiation Time:
Enterprises often require vendors to meet stringent security criteria. Having SOC 2 compliance combined with proactive pentesting can minimize back-and-forth negotiations on security concerns, speeding up the overall sales process.
Enhancing Security Posture and Risk Management
SOC 2 compliance forces an organization to adopt a disciplined security framework that provides tangible benefits beyond just an audit report:
- Improved Control Environment:
The SOC 2 process involves a thorough review of your security controls, policies, and procedures. This rigorous evaluation helps identify weak points and drive improvements. - Continuous Improvement:
SOC 2 is not a one-off certification; it demands regular reassessments. This continuous cycle ensures that your security measures evolve alongside emerging threats. - Alignment with Regulatory Requirements:
Although SOC 2 itself is not a legal requirement, it often aligns with regulatory expectations in industries like healthcare, finance, and technology. This alignment simplifies compliance with other standards, such as HIPAA or ISO 27001. - Operational Resilience:
With documented security practices and regular monitoring, SOC 2 compliance equips your organization to handle incidents more efficiently. This operational resilience is invaluable in maintaining business continuity.
Benefits in the Context of a Broader Security Strategy
SOC 2 compliance often serves as the foundation for a broader security strategy that includes regular penetration testing:
- Real-World Verification:
While policies and controls are important, only real-world testing, such as a pentest, can reveal if those controls are truly effective. This dual approach (compliance and testing) ensures that your security posture is not just theoretical but also practical. - Cultural Impact:
Pursuing SOC 2 drives a security-focused culture throughout your organization. It encourages teams to adopt secure coding practices, regular monitoring, and prompt remediation of vulnerabilities. This culture becomes a competitive advantage as your company scales. - Investor and Partner Confidence:
A well-rounded security strategy that includes both SOC 2 and regular pentesting can impress investors and strategic partners. It shows that your organization takes security seriously and is proactive in mitigating risks.
How Penetration Testing Can Accelerate Sales and Enhance Security
While SOC 2 compliance is a strong selling point on its own, pairing it with robust penetration testing can further enhance both your security posture and market competitiveness. Here are some real-world examples and reasons why startups should consider regular pentesting:
Accelerating B2B Sales with Penetration Testing
- Closing Enterprise Deals:
Many enterprise clients require vendors to provide recent pentest reports as part of their due diligence process. For instance, one SaaS startup nearly lost an enterprise deal because they lacked a current pentest report. After commissioning a comprehensive pentest and sharing the clean report, they successfully closed the deal. This real-world scenario highlights how pentesting can be a deal-clincher by removing security doubts and building trust quickly.
- Shortening Sales Cycles:
With both SOC 2 compliance and a recent pentest report, your sales team can move faster. Instead of lengthy discussions around security risk, the presence of these documents immediately reassures potential clients that your product is robust and secure. This not only reduces the time spent in vendor evaluations but also minimizes the number of security-related questions during contract negotiations.
- Client Retention and Upselling:
Clients who know that you are committed to regular security testing are more likely to trust your services in the long term. A solid security record—backed by both SOC 2 and pentest reports—can open opportunities for upselling additional features or services, as clients view your organization as a secure and reliable partner.
Enhancing Security Posture Through Penetration Testing
- Real-World Vulnerability Discovery:
Penetration tests simulate attacks on your system, uncovering vulnerabilities that automated scans might miss. For example:- Business Logic Flaws: A pentester might discover that a simple input manipulation could let a user bypass critical workflow steps.
- Misconfigurations: Even small errors in cloud security settings can be exploited; pentesting helps identify these issues before a breach occurs.
- Improved Response and Remediation:
When vulnerabilities are identified through a penetration test, they provide valuable feedback to your development and security teams. This enables you to:- Update coding practices based on real-world attack scenarios.
- Enhance incident response plans by understanding how an attacker might move laterally through your network.
- Prioritize fixes based on the risk level and potential impact of the discovered vulnerabilities.
- Regulatory and Compliance Alignment:
Even though SOC 2 does not require pentesting outright, many of its criteria (such as those related to continuous monitoring) can be validated by periodic pentests. This helps ensure that your operational controls remain effective over time. Organizations that include regular penetration testing often find it easier to demonstrate compliance during the audit period, reinforcing the overall value of SOC 2 to their security program.

Practical Examples from the Field
Consider these examples drawn from real-world experiences and insights shared by Software Secured:
- Example 1 – Sales Enablement:
A B2B startup in the fintech space was preparing for a SOC 2 Type II audit. During the sales cycle, a potential enterprise client demanded evidence of a recent pentest. Although SOC 2 Type II already required ongoing control monitoring, the additional pentest report provided the client with tangible proof of security. The result? Not only was the deal secured, but the sales cycle shortened significantly because the client’s security concerns were immediately addressed.
- Example 2 – Operational Resilience:
Another startup, after completing a SOC 2 Type I audit, chose to schedule a comprehensive pentest. The test revealed an overlooked misconfiguration in a cloud environment—an issue that could have led to data exposure. By addressing this vulnerability promptly, the startup improved its security posture, avoided potential breaches, and demonstrated proactive risk management to both auditors and investors.
- Example 3 – Investor Confidence:
Investors increasingly scrutinize the security practices of potential portfolio companies. A startup that combined SOC 2 compliance with quarterly penetration testing demonstrated a commitment to security that impressed venture capital firms during due diligence. This dual approach not only minimized risk but also enhanced the company’s valuation by showcasing a mature and evolving security program.
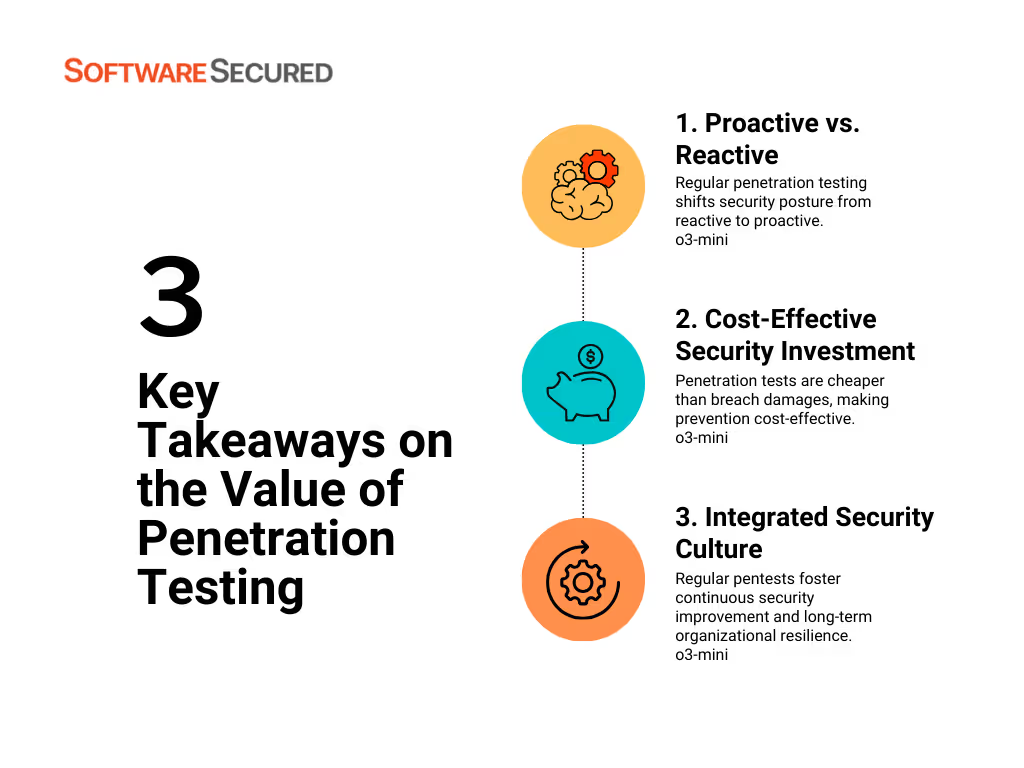
Key Takeaways on the Value of Penetration Testing
- Proactive vs. Reactive:
Regular penetration testing transforms your security posture from reactive—fixing issues only after a breach—to proactive, where vulnerabilities are identified and remedied before they can be exploited.
- Cost-Effective Security Investment:
The cost of a penetration test is generally far lower than the potential financial, reputational, and operational damage from a data breach. This investment pays off by preventing incidents that could cost significantly more in the long run.
- Integrated Security Culture:
The process of performing pentests regularly instills a culture of continuous improvement and security awareness throughout your organization. This cultural shift can help you build long-term resilience against evolving threats.
Structuring a Combined SOC 2 and Penetration Testing Strategy
To get the best of both worlds, consider the following approach:
1. Plan for SOC 2 Compliance Early:
- Establish policies and procedures that align with SOC 2 requirements.
- Identify areas that might benefit from additional testing, such as penetration testing, and schedule these as part of your compliance timeline.
2. Integrate Penetration Testing into Your Audit Cycle:
- For SOC 2 Type I, perform a baseline penetration test to document your security posture at the start.
- For SOC 2 Type II, schedule multiple tests throughout the audit period to ensure controls remain effective over time.
3. Leverage Penetration Test Results for Continuous Improvement:
- Use the detailed findings from pentests to update your security policies, patch vulnerabilities, and train your staff.
- Incorporate lessons learned into future risk assessments and security planning sessions.
4. Communicate Security Posture Internally and Externally:
- Share key metrics and outcomes from your pentest reports with your board, investors, and potential clients.
- Use these reports as part of your marketing and sales collateral to build trust and credibility.
5. Adopt a Multi-Layered Security Approach:
- While SOC 2 and pentesting are critical, combine them with other security measures like continuous vulnerability scanning, employee training, and incident response planning.
- This holistic approach not only meets compliance but also creates a resilient defense-in-depth strategy.

Conclusion: SOC 2 + Penetration Testing = A Robust Security Strategy
In conclusion, while penetration testing is not a mandatory requirement for SOC 2 compliance, it is an invaluable tool in the security toolkit of any B2B startup. SOC 2 provides the compliance stamp that builds trust and opens business opportunities. However, to truly ensure that your controls work effectively in the real world, incorporating regular penetration testing is a best practice that goes far beyond mere compliance.
For technical leaders like CTOs, CEOs, and VPs of Engineering, the combined strategy of SOC 2 compliance and proactive pentesting delivers multiple benefits:
- Strengthened Security Posture:
Regular pentests uncover hidden vulnerabilities and validate that your controls are effective, ensuring your organization is secure in practice.
- Accelerated Sales:
With documented evidence of security testing, your organization can shorten sales cycles and close enterprise deals faster by addressing customer concerns upfront.
- Enhanced Investor Confidence:
A mature security program that integrates SOC 2 with frequent pentesting instills confidence among investors and partners, setting your company apart in a competitive market.
- Continuous Improvement:
A dual approach drives a culture of ongoing security awareness and resilience, making your organization better equipped to handle future threats.
Ultimately, combining SOC 2 with regular penetration testing not only satisfies auditors and meets market expectations—it also fortifies your defenses against ever-evolving cyber threats. By investing in both, you ensure that your organization’s security is robust, verifiable, and capable of growing alongside your business. As the cybersecurity landscape continues to change, staying proactive is the best way to remain resilient and competitive.
For more insights and detailed strategies on integrating SOC 2 compliance and penetration testing, explore resources from Software Secured and related industry experts. Their guidance can help you tailor a security program that meets both compliance and operational excellence—empowering your startup to achieve long-term success in a trust-driven market.

.avif)