The Best of Both Worlds: Combining Pentesting and Bug Bounties for Maximum Security
Learn how bug bounty programs paired with pentesting can help make the most our of your security program.
TL;DR:
- Bug bounty programs incentivize ethical hackers to find vulnerabilities in applications, while penetration testing measures an application's resilience to attacks.
- Bug bounty programs offer continuous testing but can introduce risks, while penetration testing provides a structured evaluation with trusted experts.
- Other types of application security testing include vulnerability scanners, SAST, DAST, RASP, IAST, red teaming, secure code review, and SCA.
- Responsible ethical disclosures are crucial for bug bounty programs and penetration testing, ensuring vulnerabilities are addressed appropriately.
- Organizations should choose a security testing strategy that aligns with their specific needs, goals, and compliance requirements.
Bug Bounty Programs
Bug bounty programs are a way to incentivize ethical hackers to find security vulnerabilities in applications. Companies offer financial rewards, known as bounties, for vulnerabilities found at different severity levels. Bug bounty programs are often used with penetration testing to enhance overall security resilience. These programs have an element of responsible disclosure, where hackers must notify the company of the vulnerability and give them time to patch it before going public. Bug bounty programs have pros and cons:
Pros:
- There is no need to allocate a dedicated security person as the hacker provides details on the vulnerability.
- It offers an always-on type of testing, inviting ethical hackers to find new vulnerabilities.
- Allows control over the PR narrative by setting a deadline for disclosure.
Cons:
- Unknowns about the hacker's experience and reputation, posing a risk of malicious intent.
- Lack of stability and predictability in finding vulnerabilities.
- Uncapped financial liability as the bounties can add up quickly.
Penetration Testing
Penetration testing is a planned and comprehensive way to measure an application's resilience to attack. It involves ethical hackers attempting to find as many vulnerabilities as possible within a specified testing period. Penetration tests can be conducted in different types, including white-box, black-box, and grey-box testing.
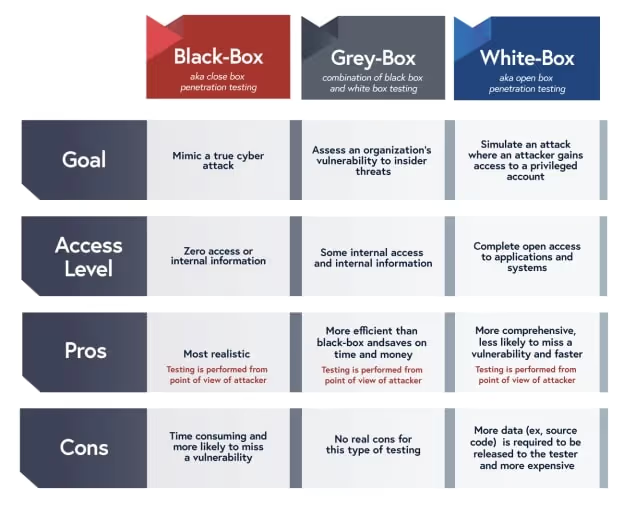
Here are the pros and cons of penetration testing:
Pros:
- Planned in advance, allowing developers to dedicate time to support the test and remediate critical vulnerabilities immediately.
- Provides a detailed report with replication steps, impact assessment, and mitigation recommendations.
- Ensures the tester is vetted and trusted, guaranteeing the quality of the report.
Cons:
- Testing occurs for a limited time and within the agreed scope, leaving potential vulnerabilities outside of the testing period.
- Higher upfront cost compared to bug bounty programs, as the fee is based on the size and scope of the application.
Other Types of Application Security Testing
In addition to bug bounty programs and penetration testing, there are other types of application security testing available:
- Vulnerability scanners
- Static application security testing (SAST)
- Dynamic application security testing (DAST)
- Runtime application self-protection (RASP)
- Interactive application security testing (IAST)
- Red teaming
- Secure code review
- Software composition analysis (SCA)
Choosing the Right Testing Approach
The choice between bug bounty programs and penetration testing depends on specific needs and goals:
- For compliance requirements, a bug bounty program alone may not be sufficient. A certificate from a vendor proving external assessment of application security is often required. Penetration testing is recommended for most compliance frameworks.
- To scale code deployment, bug bounty programs can be paired with penetration testing. The bounty program covers gaps between pentests, while penetration testing provides more detailed coverage and connects with ethical hackers for testing and remediation support.
- Penetration testing as a service (PTaaS) offers a comprehensive alternative. It involves quarterly testing, security consulting, unlimited re-testing, and rotating pentesters to maintain a fresh perspective. PTaaS combines the benefits of bug bounty programs and annual pentesting.
Responsible ethical disclosures are a crucial security requirement and best practice for organizations of all sizes. Startups and scaleups can implement such disclosures by adhering to a set of recommended steps. These guidelines ensure that security vulnerabilities are reported and addressed in a manner that protects both the organization and its stakeholders.
Effectively Responding to Responsible Ethical Disclosures in Bug Bounty Programs
Responsible Ethical Disclosure policies drive Bug Bounty programs; allowing ethical security researchers to responsibly disclose vulnerabilities found within the company's application or environment, for a predetermined price per vulnerability. Compliance frameworks such as SOC 2 don’t require a company to have a Bug Bounty program, but any company under the framework does require a Responsible Ethical Disclosure policy. Companies without a Bug Bounty program, aligned with compliance frameworks like SOC 2 will still have a Responsible Ethical Disclosure Policy and a process that includes these steps:

Effective Steps to Respond to Responsible Ethical Disclosures
1. Verify the sender:
- Check the credibility of the security researcher.
- Look for information that can help identify their credentials.
- Determine if they have conducted bug bounties in the past and the credibility of their reports.
2. Verify the vulnerability:
- Examine various aspects of the vulnerability to determine its severity and applicability.
- Request more details about the vulnerability, such as the affected system or application.
- Assess the potential impact if the vulnerability were to be exploited.
- Ask for step-by-step instructions to reproduce the issue.
- Inquire if the vulnerability has been successfully exploited or disclosed to any other party.
- Consider any specific configurations or conditions required to exploit the vulnerability.
- Request evidence or documentation to support their claims.
- Check if there are any known instances of the vulnerability being exploited in the wild.
3. Verify with a third party:
- Seek another opinion from a trusted security professional.
- Consult with your internal security team or a third-party security professional specializing in penetration testing or scaling security programs.
4. Determine scope, SLAs, and parameters:
- If compliance frameworks like SOC 2 or ISO27001 drive your Responsible Ethical Disclosure policy, define the scope of the audit.
- Consider including freemium applications and the corporate website in the scope for reputational, financial, and security risk assessment.
- Customize service level agreements (SLAs) based on the amount of sensitive data that could be exposed in a cyber attack.
- Set response time windows for different severity levels of vulnerabilities.
5. Respond to the security researcher:
- If you do not have a Bug Bounty Program, inform the researcher that you are committed to improving security but cannot provide financial compensation.
- If you are building a Bug Bounty Program, express gratitude for their assistance and offer a financial reward based on the severity of the vulnerability.
A sample templated response if you do not have a Bug Bounty Program:
Hi (ethical security researcher’s name),
Thanks for this. (Company name) is committed to working with the broader community of security professionals to continue improving our security posture.
We conduct regular penetration testing on all applications and infrastructure in scope for our Responsible Ethical Disclosure Program with a trusted vendor.
At this time we do not run a Bug Bounty program and therefore are not in a position to provide financial compensation.
Thanks for your understanding.
(Name)
A sample templated response if you are building a Bug Bounty Program:
Hi (ethical security researcher’s name),
Thanks for this. (Company name) is committed to working with the broader community of security professionals to continue improving our security posture.
Given the severity of this vulnerability and the data we protect, we are able to provide a financial reward of x. I’ve cc’d our financial team to discuss the next steps for payment.
Thanks for your assistance.
(Name)
6. Determine payouts per vulnerability:
- After remediation efforts, decide on possible payouts for the vulnerabilities.
- Consult cybersecurity experts to navigate this decision.
- Payouts depend on the severity and impact level of the vulnerability, as well as the sensitivity of the exposed data.
For example, if a company is in a highly regulated industry such as healthcare, security or financial services they can offer up to 100% more for a Bug Bounty than companies who do not; anywhere from $500 to $5,000 per vulnerability depending on the severity and impact level.
Companies that do not work with sensitive data, are less regulated and in an earlier stage of growth can pay anywhere from $250 to $2,500 depending on severity and impact level. This range can vary significantly, and it is best to consult a cybersecurity expert to confirm the standard payout per vulnerability for your organization.
7. Stay updated with the Bug Bounty landscape:
- Understand that payouts per vulnerability and the Bug Bounty market are constantly changing.
- Consult cybersecurity experts to confirm the standard payout per vulnerability for your organization.
- Stay informed about the growth and trends in the Bug Bounty industry.
Both bug bounty programs and penetration testing are essential tools for improving application security, each with its advantages and challenges. Bug bounty programs offer continuous, real-time testing by incentivizing ethical hackers to discover vulnerabilities, but they can also introduce risks such as unpredictable costs and potential malicious intent from unknown hackers. Penetration testing, on the other hand, provides a structured, comprehensive evaluation with trusted experts but is limited by its scope and time constraints. To optimize security, organizations can combine these methods or use alternative testing approaches, such as vulnerability scanners and secure code reviews. Implementing a responsible ethical disclosure policy is critical for ensuring vulnerabilities are addressed appropriately, regardless of whether a bug bounty program is in place. Ultimately, the choice of security testing strategy should align with an organization's specific needs, goals, and compliance requirements.




