How Penetration Testing Can Make Your Development Team More Productive
Learn more about how penetration testing can make your development team more productive and the best ways to implement it into you SDLC.
While penetration testing is often just used to check a security box, it can also significantly enhance productivity in the development process. By identifying and resolving vulnerabilities early on in the SDLC, penetration testing can help development teams develop secure coding practices which reduce rework and avoid delays, build-up collaboration and communication, and improve customer relationships. Understand how penetration testing can make your development team more productive and develop secure coding practices.
In this blog post, we will explore how penetration testing can make your development team more productive, but also the other critical benefits beyond productivity. We will dive deep into…
- The benefits of penetration testing
- How to implement penetration testing into your development process
- The benefits penetration testing can bring beyond just productivity.
By the end of this post, you will understand why penetration testing is not only crucial for security reasons –but also for increasing effectiveness in the development process.
Ways penetration testing boosts productivity within the development team
Spotting and fixing vulnerabilities at an early stage
One of the significant benefits of penetration testing is that it allows for the early identification and resolution of vulnerabilities in the development process. Rather than discovering vulnerabilities during the later stages of development or, worse yet, after a product has been released, penetration testing can be done in the design or testing stages before new code is even released to production.
Only 25% of organizations with low-security integration can remediate a vulnerability within 1 day, compared to 45% of organizations with high levels of security integration. By integrating penetration testing early into the SDLC, you can remediate vulnerabilities faster and more cost-efficient than those who have lower security integrations.
When you can identify vulnerabilities in the early stages of development, not only do you avoid costly reworks and revisions, but you also avoid the costs associated with finding the vulnerabilities later. The average cost of finding vulnerabilities in the design phase is approximately $500.00. When vulnerabilities are caught in an earlier stage, developers have the opportunity to understand, digest and learn where their coding errors arose from, and how to avoid them in the future. When vulnerabilities are caught at a later stage, the costs are increased exponentially. The cost to fix vulnerabilities in the maintenance stage is 100 times more than the cost of finding a vulnerability in the design phase.
Over time, developers will begin to learn how to avoid vulnerabilities found in the early stage of development, making the team overall more productive and more cost-efficient. Conducting quarterly penetration testing is essential so teams can ensure that their code is secure, reliable, and less prone to errors, ultimately leading to a more productive development process.
Minimizing redo work and preventing delays
52% of organizations report sacrificing cybersecurity for speed-to-market. To avoid these delays, developers continuously evaluate where they can speed up processes. Cybersecurity is a large blocker and is often deemed an “easy” sacrifice to push products to market. This can lead to much bigger issues when the product is live in the market without proper cybersecurity validations, such as a vulnerability being found. When vulnerabilities are exploited, hackers can usually go undetected for months without anyone noticing.
The average time for a team to detect a breach in their system is 277 days. This means a hacker has over 9 months of undetected access to your system and sensitive client information.
Fostering teamwork and effective communication
When you involve the security team in the development process, developers can gain a better understanding of potential security risks and integrate security measures into their code early on. This collaboration can lead to more effective and efficient code development, reducing the likelihood of security issues and enabling teams to move forward with confident secure coding. Improving communication between security and dev teams has been an ongoing challenge and is not easy to navigate.
Here are some tips to help cultivate a collaborative and communicative environment between security and dev teams:
- Building a shared responsibility for security
- Expanding observability
- Setting policies that account for both teams
- Encouraging mutual empathy, understanding, and feedback
- Ensuring transparency on decisions and progress
- Bonus: Injecting fun into security
As you continue to work together to solve security coding issues, seize opportunities to educate, communicate and collaborate from both sides. You should strive to have an ongoing path towards cohesion, and goals/objectives should be re-evaluated and audited twice a year (if not more) to move both teams towards common goals.
Steps to integrate penetration testing into the development workflow
Integrating penetration testing into the development process requires careful planning and execution to be effective. It is essential to establish a process for annual or quarterly penetration testing throughout the development lifecycle. This can include defining the scope of the penetration test and establishing guidelines for interpreting and addressing the results. It is also crucial to ensure that the penetration testing process does not disrupt the development process or delay timelines. You can avoid delays and disruptions in a variety of ways, but it is best to communicate with your penetration testing vendor, as your application's functionality and testing priorities are unique in every situation.
The best implementation approach involves conducting manual penetration testing at various stages of the development process, such as during code integration, testing, and deployment. This integration enables development teams to identify and resolve vulnerabilities in real time, allowing for a more efficient and secure development process.
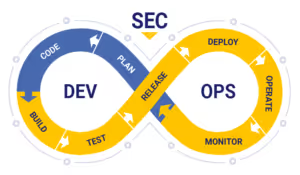
It is recommended that you hire a credible, third-party professional penetration testing team. These teams are experienced in identifying vulnerabilities and can provide valuable insights and recommendations for improving the security of your development process and your product. By leveraging their expertise, development teams can save time and resources, improve the overall security posture, and ensure that their products are secure from the start, with verification at every stage.
Advantages of penetration testing that go beyond just productivity
While improving productivity is undoubtedly a significant benefit of penetration testing, other benefits make it a critical component of any development process.
Strengthening cybersecurity posture
Penetration testing can help strengthen your overall cybersecurity posture. By conducting penetration testing on a quarterly or semi-annually basis, development teams can identify and address vulnerabilities before they are exploited by attackers. This proactive approach can help prevent data breaches, protect sensitive information, and ultimately, safeguard your organization's reputation.
Ensuring regulatory compliance
Penetration testing can help you meet compliance requirements. Many regulatory bodies (SOC 2, ISO 27001, PCI DSS, HIPAA etc.)require organizations to conduct regular security testing to ensure that their products and services meet specific standards. The General Data Protection Regulation (GDPR) non-compliance fines hit nearly $100 million in the first half of 2022 alone, and by introducing quarterly penetration testing you reduce your chances of violating compliance regulations.
Building customer confidence, trust and loyalty
Penetration testing can help build customer trust and loyalty. In today's digital age, customers are increasingly concerned about the security and privacy of their data. 50% of Americans have decided not to use a product or service due to personal privacy concerns. By demonstrating a commitment to security through regular penetration testing, you can build trust with your customers and differentiate yourself from competitors who may not take security as seriously. Vulnerabilities and defects have a large impact on the user experience, a Centrify study found that 65% of data breach victims lost trust in a company as a result of the breach. When companies demonstrate their commitment to security, this trust initiative can translate into increased customer loyalty, repeat business, and positive word-of-mouth recommendations.
In summary
Beyond security, penetration testing helps your development team become a cohesive and effective team. When penetration testing is properly integrated into the SDLC, you can reap larger organizational benefits alongside inner departmental wins. Learning how penetration testing can make your development team more productive by implementing secure coding practices. Now that you know how to implement penetration testing, what about developing secure coding practices? Developing secure coding within your dev team shifts your security left to a more proactive approach, and will reduce a lot of code-related security errors.



.avif)

