Penetration Testing ROI: 5 Metrics to Communicate Real Value
Learn how to communicate the penetration testing return on investment to your CFO by using these 5 key metrics.
Penetration testing is a proactive security practice designed to uncover vulnerabilities before malicious attackers can exploit them. In this post, we’ll break down what penetration testing entails, how it’s performed, and why it’s a crucial component of any comprehensive security strategy. For further insights, visit our blog on SoftwareSecured.
At its core, penetration testing is a simulated cyberattack on your systems, networks, or applications. Its primary goal is to identify security weaknesses that could be exploited by real-world attackers. Unlike a general vulnerability assessment, penetration testing actively exploits vulnerabilities in a controlled manner to demonstrate their potential impact.
Penetration tests can be tailored to suit different scenarios and attack perspectives. Common testing approaches include:

These flavours, which mimic various attack scenarios, help organizations understand how different threat actors might approach their systems. More about our approach can be found on our services page.
Beyond the testing approaches, penetration testing is often categorized by the target environment. Key types include:
A structured methodology is crucial for an effective penetration test. The typical process involves:
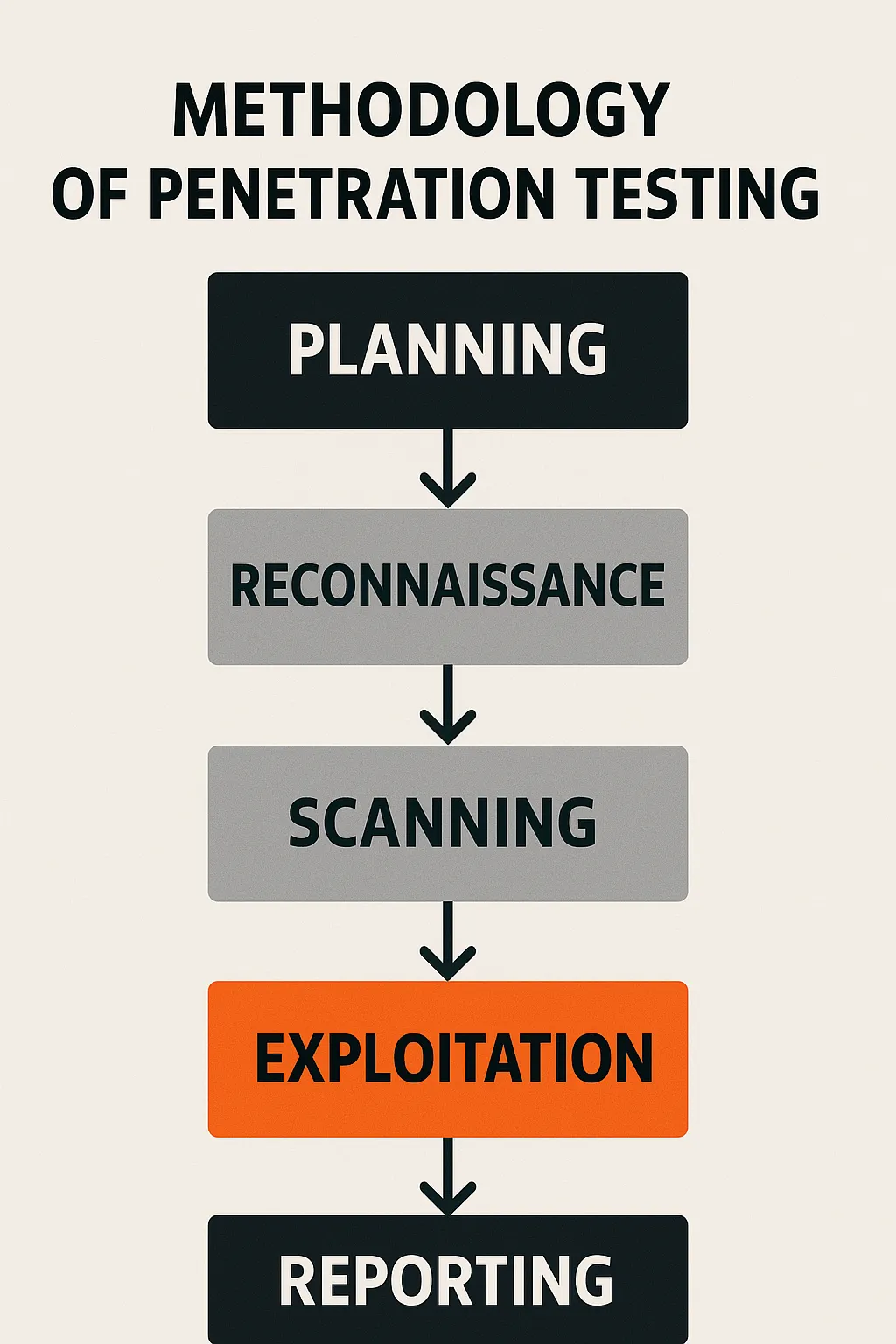
Each step provides actionable insights that help organizations improve their security posture. More details on our testing process are available on our process page.
Penetration testers rely on a blend of industry-standard tools and expert manual techniques. Some common tools include:
While automated tools streamline testing, manual techniques are essential for discovering complex vulnerabilities. For an overview of the tools we use, explore our services.
Given the intrusive nature of penetration testing, adhering to legal and ethical guidelines is paramount:
Benefits:
Limitations:
Understanding these factors helps organizations set realistic expectations and continuously improve their security measures. For further insights on our testing benefits, visit our blog.
Real-world case studies highlight how effective penetration testing can uncover critical vulnerabilities and drive strategic improvements. Below are a few examples of real-world case studies:
For additional examples and success stories, browse through our extensive case studies library.
In today’s rapidly evolving threat landscape, regular penetration testing is not just an optional extra—it’s a strategic necessity. By simulating real-world attacks, organizations can identify vulnerabilities, improve their security posture, and better prepare for potential threats.
Best Practices Include:
.webp)
Sherif Koussa is a cybersecurity expert and entrepreneur with a rich software building and breaking background. In 2006, he founded the OWASP Ottawa Chapter, contributed to WebGoat and OWASP Cheat Sheets, and helped launch SANS/GIAC exams. Today, as CEO of Software Secured, he helps hundreds of SaaS companies continuously ship secure code.
Security
Can be easily manipulated without detection if not properly secured.
Digitally signed and can be validated on the server. Manipulation can be detected.
Size
Limited to 4KB.
Can contain much more data, up to 8KB.
Dependency
Often used for session data on the server-side. The server needs to store the session map.
Contains all the necessary information in the token. Doesn’t need to store data on the server.
Storage Location
Browser cookie jar.
Local storage or client-side cookie.
Compare OpenID Connect, SAML v2.0, and OAuth 2.0. Understand key differences, roles, and security risks in modern federated identity systems.


Providing the quality of the biggest names in security without the price tag and complications.
Manual penetration testing
Full time Canadian hackers
Remediation support
