How Threat Modeling Adds Value to a Penetration Test
Read this article to understand the benefits of threat modeling for penetration testing and how Software Secured integrates threat modeling.
Data is the new currency! Conspicuously, its weight and importance are the reason and motivation for hackers to breach the security of a system. But lucky for us, we have several approaches to strengthen our defences. We’ll be discussing 2 such approaches in this article - threat modelling and penetration testing, and then discuss the benefits of threat modelling for penetration testing.
Understanding Threat Modeling
Threat modelling is a distinctive proactive process of detecting and identifying potential threats and vulnerabilities that put a system and its elements at risk. It involves analyzing the system or application from the perspective of an attacker and identifying potential weaknesses in its design, implementation, or operation that could be exploited to compromise its security. Threat modelling plays a crucial role in enhancing security by proactively identifying potential risks and vulnerabilities within an organization, network, or application. This process enables the implementation of targeted countermeasures and mitigating controls to address specific threats effectively. By conducting regular threat assessments, organizations can allocate resources efficiently, focusing on the most critical vulnerabilities and prioritizing security efforts.
A Comprehensive Guide to Threat Modeling for Pentesting
Threat modelling, often perceived as a complex process, can be simplified into manageable steps. Many people initially find the concept intimidating, but breaking it down into workable tasks makes it systematic and approachable, even for complex architectures. This methodical breakdown not only demystifies the process but also makes it more accessible to those who might otherwise be deterred by its perceived complexity. Ultimately, threat modelling becomes a structured and achievable practice when approached with a clear, step-by-step methodology.
Threat modelling typically involves the following steps:
- Identifying the system or application to be analyzed
- Creating a data flow diagram to understand how data flows through the system or application
- Identifying potential threats and vulnerabilities at each step in the data flow diagram
- Prioritizing the identified threats and vulnerabilities based on their severity and likelihood of occurrence
- Developing mitigation strategies to address the most critical threats and vulnerabilities
Threat modelling can be incorporated into the design, development, and testing phases. Using threat modelling at the initial stages of the project comparatively exhibits a higher rate of mitigating threats.
Exploring the Basics of Penetration Testing
Penetration testing is a cybersecurity technique that simulates a cyber attack to evaluate any vulnerabilities that could be exploited. The idea of a simulation is to understand the mindset and course of action of cybercriminals and put into perspective the steps to be taken to protect against attacks.
There are 7 stages in the process of penetration testing:
- Reconnaissance: Gathering information about the target system or application.
- Threat Modeling & Custom Security Plan: Conduct light threat modelling and analyze unique business cases to build a custom security plan.
- Automatic & Custom Script Developments: Start diving deep into the application with a mix of manual and automated approaches.
- Identification of Zero-day Vulnerabilities: As critical vulnerabilities are identified, the client is notified immediately. Steps to reproduce the issue are shared with the client so that their development team can begin remediation as soon as possible.
- Exploitation and Escalation: The less severe vulnerabilities found during the early stages of the pentest are exploited and escalated as much as possible without affecting the function of the application.
- Cleanup and Reporting: Upon completion, pentesters will gather all found issues, regardless of severity, into a report. A good penetration testing provider should also include steps for replicating the issue so that the client’s development team can mitigate the issue.
- Retesting and Certification: After the report is delivered, the client may patch several vulnerabilities. A quality pentest provider will be able to retest these known vulnerabilities shortly after to verify that they have been fixed correctly or sufficiently, and then the pentest provider can offer a certificate to the client as proof of application security.
Threat modelling typically fits in early in the penetration testing process, ideally during the scoping and planning phase. This is because threat modelling can help identify and prioritize potential threats and attacks that the penetration test should focus on. To understand better, let's delve a little deeper into the benefits of threat modelling for penetration testing.
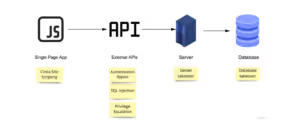
Enhancing Security Assessment by Incorporating Threat Modeling into Penetration Testing
Incorporating threat modelling into penetration testing enhances security assessments by systematically identifying potential threats and vulnerabilities. The process begins with a comprehensive analysis of the system's architecture, data flows, and potential attack vectors. Security controls are then developed to address identified risks, focusing on critical assets and high-impact scenarios. A thorough penetration test is executed, leveraging the insights gained from threat modelling to target specific vulnerabilities and assess the effectiveness of implemented controls. Results are meticulously analyzed, and identified issues are prioritized for remediation based on their potential impact and likelihood. To maintain a robust security posture, continuous monitoring is essential, with periodic repetition of the threat modelling and penetration testing cycle to address evolving threats and system changes. The infiltration of a system or an application can cause serious damage, entailing severe repercussions with huge losses. The conjunction of using threat modelling to a penetration test will combine the forces of both security practices. While penetration testing at an organizational level communicates that it is taking the necessary measures to ensure the safety of its data, the addition of a threat model will only magnify the strength.
Maximizing the Value of a Penetration Test with Threat Modeling
The detection of initial threats and potential attack points paves the way for a penetration test. Threat modelling can add value to a penetration test in several ways:
- It can help penetration testers identify the most critical areas to test by prioritizing potential threats and vulnerabilities based on their severity and likelihood of occurrence.
- Threat modelling can help penetration testers gain a better understanding of the system or application being tested by analyzing it from an attacker's perspective.
- It can help identify potential vulnerabilities and attack vectors that may have been missed during the initial scoping and planning stages of the penetration test.
- By identifying the most critical threats and vulnerabilities, threat modelling can help organizations prioritize their remediation efforts to address the most significant risks first.
- Threat modelling is a proactive approach to security that can help organizations identify and address potential security risks before they can be exploited by attackers.
- It forces both the penetration testing team and the organization to think about all kinds of threats and vulnerabilities that may be present in the system or application.
- Threat modelling can help identify blind spots in the testing process and reveal social engineering or other threat possibilities that aren’t necessarily tied to the scope of the penetration test.
- A proper threat modelling session can help organizations understand the business risks in more quantitative terms. It also gives organizations a better idea of their assets and the risks associated with them. This improves the overall outcome of security testing.
Incorporating threat modelling into the penetration testing process can add significant value to both the penetration testing team and the organization. Now that we’ve understood the benefits of threat modelling for penetration testing, let’s understand how Software Secured does threat modelling.
The Role of Threat Modeling in Software Secured's Penetration Testing
At Software Secured, we believe that threat modelling is an essential part of any effective security testing methodology. Software Secured has a tried and tested approach to threat modelling that we use to help our clients better understand their security risks.
Our approach to threat modelling is based on three main components that we build alongside the client: assets, threat actors, and connections and data flow.
Identifying Assets in Threat Modeling for Pentesting
The first step in our threat modelling process is to identify and categorize the client's assets. These could include web applications, databases, servers, and any other systems or components that are critical to the client's business operations.
Analyzing Threat Actors in the Context of Pentesting
The next step is to identify all potential threat actors, both external attackers and some internal ones like employees, clients, marketing tools, and third-party libraries. We also explore the concept of island hopping in detail.
Understanding Connections and Data Flow in Threat Modeling for Penetration Testing
Finally, we map out the connections and data flow between the various assets and threat actors. This is important information that helps us identify all possible attack vectors. Understanding the moving parts allows attackers to go beyond what static analysis/vulnerability scanners can do. An effective model is built on this kind of "insider" information.
Once we have a clear picture of the client's assets, threat actors, connections, and data flow, we use STRIDE (or other threat models) to categorize potential threats. By using threat models, we can categorize potential threats and prioritize what to test and how to test.
Threat modelling helps us to focus our testing efforts on the most critical areas of the client's system or application. By identifying potential threats and vulnerabilities, we can develop effective strategies to manage or mitigate these risks. By building a comprehensive threat model alongside our clients, we can help them better understand their security risks and develop effective strategies to manage them.
Drawing Insights from Threat Modeling for Penetration Testing
Threat modelling is a valuable exercise that can enhance the effectiveness and efficiency of a penetration test. While it is true that threat modelling may not capture all possible attack vectors, it is still a valuable tool for identifying and mitigating a wide range of potential vulnerabilities. By combining threat modelling with penetration testing, organizations can achieve a more comprehensive understanding of their system's security posture. The amalgamation of threat modelling and penetration testing is analogous to two mighty heroes combining forces to defeat the villain in the climax of an excellent comic book. Isn’t it just wonderful when two heroes finally come together?!
While a pentest is typically limited in scope and focused on specific applications, threat modelling can be more focused or company-wide, covering all risks, including social engineering. By identifying potential threats and risks to a system, threat modelling helps both the organization and the pentester gain a deeper understanding of the security posture and potential attack scenarios. In an era where attackers are getting more creative and skillful, we need to get all the big guns out, and threat modelling for penetration testing could be one of your biggest guns!




.avif)
.avif)