Network Full Protection: The Role of Internal and External Network Pentesting
Discover the differences between internal and external network pentesting, their methodologies, and their risks.
In this article, we will discuss the concepts of internal and external network penetration testing.
Exploring the Objectives and Coverage of Internal and External Network Penetration Testing
Let's imagine the penetration testing as an organized attack, but this time on your assets. It is meant to assist in the identification of weaknesses in advance of a malicious attack.
- In simple terms, Internal Network Penetration Testing works to determine the weaknesses existing in your internal network. The external border is crossed to simulate the actions of an insider threat, such as a worker, or a third party who is already in a position to bypass the external defenses. The only risks that this test determines are the ones that an attacker might utilize after intrusion into the internal environment.
- From outside the network—and let’s not forget the psychological concept of this test—within this context, External Network Penetration Testing is when a remote attacker tries to penetrate the game interface of the network. The defences aimed at repelling hostile intrusions that are available at the perimeter of the network make the objects of this kind of attack. As a preventative measure, we need to determine what weaknesses an intruder would be able to exploit to the extent that they were able to gain access to our network’s perimeter.
Highlighting the Unique Benefits of Internal Pentesting versus External Pentesting
Both testing types are crucial, but they offer different insights.
- Internal Pentesting provides an in-depth look at what could happen if an attacker is already inside your network. It evaluates internal policies, procedures, and controls, identifying areas for improvement beyond what external tests cover. It helps us understand lateral movement—how an attacker might navigate through your network to access sensitive data or systems.
- External Pentesting assesses your exposure to threats originating from outside your organization. It strengthens your perimeter defences by simulating real-world attacks from unknown external sources.
Together, these tests strengthen your overall security posture. Internal testing reveals vulnerabilities that could be exploited if external defences are breached, while external testing focuses on securing those initial entry points.
Ensuring Compliance Requirements are Met
Regulations like HIPAA, PCI DSS, GDPR, SOC 2 and ISO 27001 require organizations to protect sensitive data and conduct regular security assessments.
- Internal Security Standards Compliance: Internal penetration testing provides documented evidence that you're proactively testing and mitigating internal threats. This is essential for audits and maintaining certifications.
- Protecting Sensitive Data: For organizations handling personally identifiable information (PII), financial data, or health records, internal tests ensure this information is protected from unauthorized access by internal actors or compromised devices.
Depending on the compliance framework you are required to follow, different types of pentesting may be required.
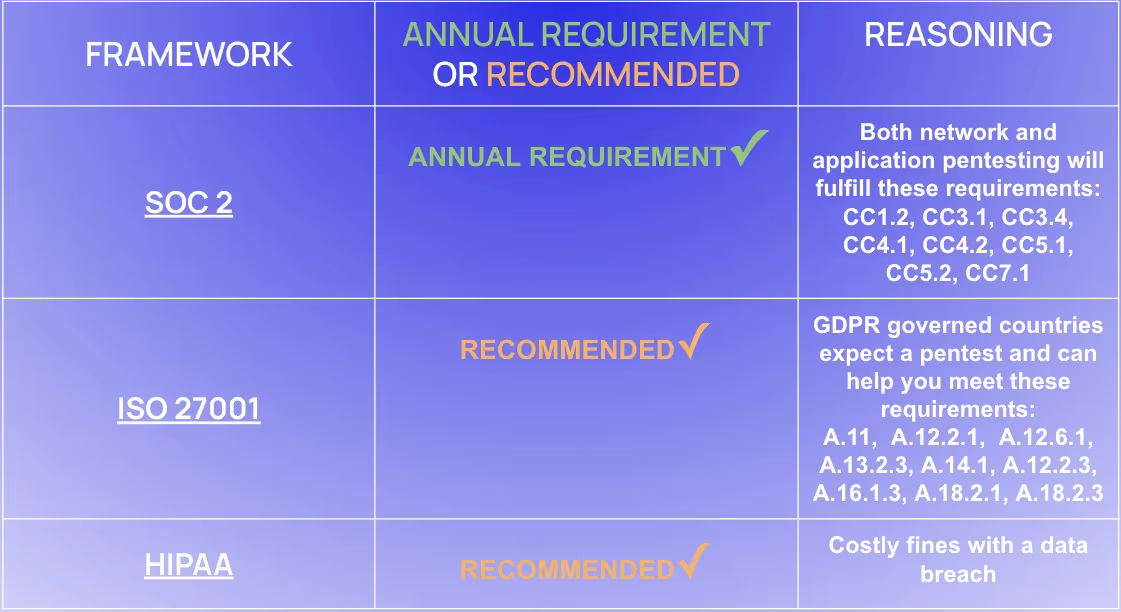
By conducting regular pentests, we not only comply with legal obligations but also build trust with our customers. It shows we're committed to safeguarding their information.
Identifying Internal Threats and Lateral Movement Risks
Internal threats aren't just about disgruntled employees. They can also be external attackers who have breached your defences.
- Lateral Movement Testing: Once inside, attackers use lateral movement to navigate through your network, seeking valuable data or privileged systems. This tests the effectiveness of your segmentation, network monitoring, and internal access controls.
- Insider Threats and Malicious Insiders: Internal testing simulates risks posed by employees, contractors, or compromised devices. It highlights vulnerabilities that could be exploited by someone with internal access, which is critical for identifying risks from social engineering or unsecured devices.
Internal penetration testing uncovers how these movements could happen. It helps us patch pathways an attacker might use, tightening our internal security.
Promoting Employee Awareness and Security Culture
Technology isn't the only defence. Our people play a critical role in security.
- Identifying Security Awareness Gaps: Internal testing often reveals weaknesses arising from employees inadvertently weakening security, such as using weak passwords or bypassing policies. These insights help inform training and improve employee security awareness.
- Reinforcing a Proactive Security Culture: Regular internal testing emphasizes that security is a priority. It encourages best practices in handling sensitive information and reinforces the importance of following internal protocols.
By fostering a culture of awareness, we reduce risks like phishing attacks and accidental data leaks. When everyone understands their role, our overall security posture improves.
Evaluating Segmentation and Access Controls through Testing
Segmenting networks is like putting valuables in different safes. If one area is breached, the others remain secure.
- Internal Network Segmentation: Internal tests validate whether network segmentation effectively prevents unauthorized movement between zones. By examining firewalls, VLANs, and access restrictions, we ensure sensitive areas like finance, HR, and production networks are well-protected from general access.
- Access Control Effectiveness: Testing verifies that internal users and systems have appropriate access controls. It ensures no unauthorized user can access sensitive data or critical systems, which is essential for compliance and risk management.
By testing these measures, we confirm that unauthorized access is prevented and that only authorized personnel can access sensitive resources.
Detecting Configuration Errors and Legacy Systems Vulnerabilities
Old systems and misconfigurations are often the weak links in security.
- Configuration Issues: Internal testing uncovers configuration errors like misconfigured access rights, poorly managed credentials, or insecure protocols (e.g., SMB, Telnet). These errors create vulnerabilities that compromise network security.
- Legacy Systems and Unsupported Software: Many organizations retain legacy systems for business continuity, but these older systems may lack robust security features. Internal testing assesses these systems for vulnerabilities, ensuring they don't become weak points for attackers.
Identifying these issues helps us update or isolate legacy systems and fix configuration errors. It's about closing doors we didn't know were open.
Conducting Data Exfiltration Testing for Network Security
Preventing data from leaving our network is just as important as keeping attackers out.
- Data Sensitivity and Exfiltration Risks: Internal tests evaluate how easily sensitive data can be accessed and extracted. This includes testing the security of data repositories and the adequacy of Data Loss Prevention (DLP) measures.
- Protection Against Common Techniques: We simulate common exfiltration methods like using compromised email accounts, web traffic masking, or encrypted transfers. This helps ensure the organization can detect and block data exfiltration attempts.
Data exfiltration testing shows us how protected our sensitive information is and helps us implement measures to stop unauthorized transfers.
Assessing Incident Response Capabilities Through Testing
Even with all defences in place, incidents can happen. How we respond makes all the difference.
- Assessing Detection and Monitoring: Internal penetration tests validate your ability to detect and respond to threats within the network. We assess whether logging, monitoring, and alerting systems effectively identify unusual or unauthorized activity in real-time.
- Incident Response Readiness: Testing reveals how prepared your organization is to handle an incident once an attacker is within the network. This includes examining how quickly threats are detected, whether proper alerts are generated and whether the incident response team responds according to protocol.
By simulating attacks, we assess our ability to detect, respond, and recover. This helps us improve response times and protocols, minimizing impact.
Highlighting the Unique Benefits of Internal Pentesting versus External Pentesting
Internal and external penetration tests complement each other, each providing unique benefits.
- Enhanced Focus on Internal Policies and Procedures: Internal pentests evaluate your internal security policies, procedures, and controls. They identify areas for improvement that external tests might not cover.
- Strengthening the Overall Security Posture: Internal testing reveals vulnerabilities an attacker could exploit if external defences are breached. External testing focuses on securing those initial entry points. Together, they provide a comprehensive view of your security landscape.
Choosing both tests ensures you're not just building walls but also securing the spaces within.
Understanding What Remains Consistent in Both Internal and External Network Pentesting
In both internal and external network penetration testing, the target remains the same. Internal and external network pentesting plays a crucial role in identifying vulnerabilities and strengthening defences. However, internal attackers may pose a greater threat as they have a deeper understanding of the network's critical systems and their locations.
Conclusion
At Software Secured, we're committed to bringing high-quality security to fast-growing software companies at a price point you can consume. Penetration testing, both internal and external, is a vital part of that mission. By understanding and applying these concepts, we can build stronger defences and foster a culture of security awareness.
If you're ready to take your security to the next level, we're here to help. Let's make your organization safer, together.




.avif)
