Executive Summary: STRIDE Threat Modelling for Secure-by-Design Architectures
Discover how STRIDE threat modelling empowers CTOs and VPs of Engineering to build secure-by-design architectures with proactive risk management and robust cybersecurity measures.
In today’s rapidly evolving digital landscape, integrating security into every phase of the software development lifecycle (SDLC) is no longer optional—it is a critical necessity. Among the many methodologies available, STRIDE threat modelling stands out as a robust framework designed to proactively identify, analyze, and mitigate potential security vulnerabilities before they can be exploited. Developed by Microsoft in the late 1990s, STRIDE continues to serve as a cornerstone for secure software design and risk management.
This document explores the STRIDE framework in depth, detailing its components, real-world applications, comparative methodologies, and strategic implementation guidelines. It is crafted for senior technical leaders who are looking to embed security deeply into their product development cycles.
The Strategic Importance of Threat Modelling
Embedding Security Early in the SDLC
Modern software development is characterized by rapid iterations, continuous integration, and frequent deployments. In this dynamic environment, waiting until post-deployment to address vulnerabilities can be both costly and risky. Threat modelling—using frameworks such as STRIDE—allows organizations to identify design flaws at the earliest possible stage. This “security-by-design” approach not only minimizes the window of exposure but also reduces remediation costs, as vulnerabilities are addressed before code is written.
By integrating threat modelling into your SDLC, you are investing in a proactive posture that continuously assesses the security posture of your systems. This not only protects critical assets but also instills a culture of security awareness across engineering, development, and operations teams.
The Broader Impact on Organizational Culture
Threat modelling is not just a technical exercise; it is a collaborative process that involves stakeholders from across the organization. Bringing together developers, architects, security experts, and even product managers ensures that multiple perspectives are considered, leading to more comprehensive security solutions. This cross-functional collaboration enhances overall security literacy, ensuring that every team member—from the front lines of development to executive leadership—is aware of potential risks and best practices.
Deep Dive into STRIDE: The Six Pillars of Threat Analysis
The STRIDE framework is built around six core threat categories. Each category addresses specific attack vectors and vulnerabilities that can compromise an application’s integrity, confidentiality, and availability.
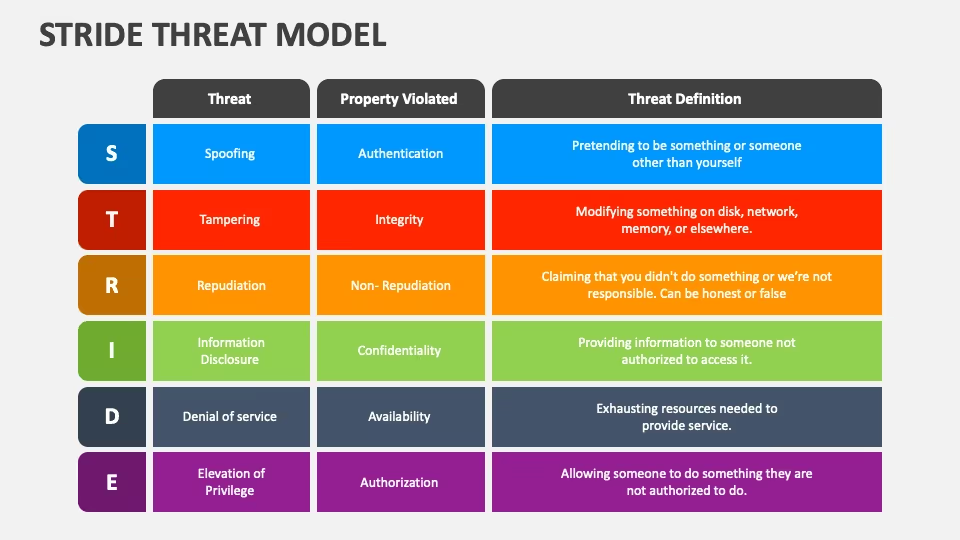
1. Spoofing
Definition & Mechanism:
Spoofing involves impersonating a legitimate entity to gain unauthorized access to systems or data. Attackers can use spoofing to trick systems into accepting malicious requests by faking identity credentials. In many cases, this is achieved through techniques like phishing, where the attacker sends emails or messages that appear to be from trusted sources.
Real-World Example:
A notorious example is the rise of AI-powered phishing attacks. Traditional phishing emails are increasingly being automated, allowing attackers to craft personalized, convincing messages that mimic legitimate correspondence. In 2020, several large organizations reported phishing campaigns that successfully bypassed conventional spam filters by leveraging machine learning to create more authentic-looking emails. These attacks not only jeopardized sensitive data but also eroded trust in communication channels.
Mitigation Strategies:
- Multi-Factor Authentication (MFA): Implementing MFA makes it significantly harder for attackers to spoof identities, as multiple verification factors are required.
- Advanced Email Filtering: Leveraging AI and machine learning to detect anomalies in email communication can drastically reduce the success rate of phishing attacks.
- User Training: Regular training programs on recognizing phishing attempts can further strengthen an organization’s defense against spoofing.
2. Tampering
Definition & Mechanism:
Tampering refers to the unauthorized modification of data, configuration files, or system logs. Attackers may alter data to hide their tracks, introduce vulnerabilities, or manipulate system behavior for malicious purposes.
Real-World Example:
Consider a scenario in which a cyber attacker gains access to a configuration file within an enterprise application. By modifying the configuration, the attacker could disable critical security settings, opening the door for further exploitation. In 2018, a major financial institution faced a data breach where tampering with logs obscured the trail of unauthorized access. This incident highlighted the need for robust file integrity monitoring (FIM) systems.
Mitigation Strategies:
- File Integrity Monitoring (FIM): Continuously monitoring changes in configuration files and system logs helps detect tampering early.
- Immutable Logging: Implementing secure, immutable logging mechanisms ensures that any unauthorized changes can be detected and traced back to their source.
- Access Controls: Strictly managing who has access to modify critical files or settings is fundamental to minimizing tampering risks.
3. Repudiation
Definition & Mechanism:
Repudiation occurs when an actor performs an unauthorized operation and then denies involvement, making it difficult to trace the action back to the perpetrator. This is often due to insufficient logging or weak audit trails.
Real-World Example:
In environments where outbound communications are not thoroughly validated, an attacker might perform malicious operations and later deny responsibility. A notable instance was observed in email systems where lack of proper logging allowed attackers to send fraudulent messages without any traceable digital footprint. This type of attack not only impairs accountability but also complicates forensic investigations.
Mitigation Strategies:
- Comprehensive Audit Trails: Implementing detailed and tamper-proof logging mechanisms can ensure that every action is recorded with a verifiable timestamp.
- Digital Signatures: Using digital signatures on transactions and communications can help validate the authenticity and non-repudiation of actions.
- Regular Audits: Periodic audits of system logs and access controls can help uncover any gaps that might be exploited for repudiation.
4. Information Disclosure
Definition & Mechanism:
Information disclosure involves the unintentional leakage of sensitive data. This can occur through insecure configurations, error messages, or even improperly secured backups. The disclosure of such data can lead to significant privacy breaches and competitive disadvantages.
Real-World Example:
One prominent example occurred when an e-commerce company inadvertently exposed database details through overly verbose error messages. This incident allowed attackers to gather critical information about the system architecture and vulnerabilities, ultimately leading to a targeted data breach. In another case, misconfigured cloud storage led to millions of records being accessible publicly, emphasizing the risk of information leakage in modern digital environments.
Mitigation Strategies:
- Secure Error Handling: Ensure that error messages are generic and do not reveal sensitive system details.
- Data Minimization: Only collect and store the data that is absolutely necessary for operations.
- Regular Configuration Reviews: Conduct periodic reviews of system and cloud configurations to ensure that they adhere to best security practices.
5. Denial of Service (DoS)
Definition & Mechanism:
Denial of Service attacks aim to disrupt the normal functioning of a service by overwhelming it with traffic or requests, thereby denying legitimate users access. These attacks can target network resources, application endpoints, or backend systems.
Real-World Example:
One of the most infamous DoS incidents occurred in 2017 when Google was targeted by an attack that involved spoofed traffic across 180,000 servers. The attacker managed to generate up to 167 million packets per second (Mpps), showcasing the potential scale of modern DoS attacks. According to industry reports, 2020 saw around 12.5 million DDoS-capable devices, and a 2022 study indicated a 133% increase in DoS incidents over the previous year. These statistics underscore the persistent and growing threat posed by DoS attacks.
Mitigation Strategies:
- Scalable Defensive Tools: Utilizing solutions such as AWS Shield or Cloudflare’s DDoS protection services can help absorb and mitigate large-scale attacks.
- Traffic Anomaly Detection: Implementing advanced monitoring systems to detect unusual spikes in traffic can enable faster response and mitigation.
- Redundancy and Load Balancing: Designing systems with redundancy and efficient load balancing can reduce the impact of an attack by distributing traffic across multiple nodes.
6. Elevation of Privilege
Definition & Mechanism:
Elevation of privilege occurs when a user or process gains access to functionalities or data beyond their authorization. This can happen due to missing authorization checks, configuration errors, or vulnerabilities in the application’s logic.
Real-World Example:
A common instance involves a minor oversight in the implementation of access controls. For example, in 2019, a software vendor discovered that a flaw in their authentication system allowed regular users to perform administrative actions simply by manipulating URL parameters. This seemingly small vulnerability had the potential to lead to a full-scale system compromise if exploited further.
Mitigation Strategies:
- Rigorous Access Control Reviews: Regularly audit access control mechanisms to ensure that permissions are strictly enforced.
- Automated Security Testing: Implement static and dynamic analysis tools as part of the CI/CD pipeline to catch authorization flaws before they reach production.
- Defense in Depth: Use layered security controls that can prevent or mitigate the impact of any single vulnerability being exploited.
Complementary Threat Modelling Methodologies
While STRIDE offers a solid foundation for threat analysis, it is important for senior technical leaders to be aware of alternative frameworks that might better suit specific use cases. Each methodology has its own strengths and focus areas:
- PASTA (Process for Attack Simulation and Threat Analysis): Emphasizes attack simulation and quantification of risk, making it well-suited for organizations that require a granular understanding of threat impact.
- VAST (Visual, Agile, and Simple Threat): Designed for large-scale environments, VAST supports integration with agile development processes and is ideal for complex, distributed systems.
- Trike: Focuses on risk management and is particularly effective in scenarios where establishing clear risk boundaries is paramount.
- OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation): Provides a comprehensive methodology that includes self-directed assessments and is beneficial for organizations looking to integrate threat analysis into broader risk management programs.
- NIST Framework: Offers detailed guidelines for risk assessment and is highly regarded for its rigor and alignment with compliance requirements.
Each of these methodologies can be tailored to address specific organizational needs. For many enterprises, a hybrid approach—leveraging STRIDE alongside elements from these frameworks—can provide a more comprehensive view of the threat landscape.
1. Implementing STRIDE in Your Organization
2. The Process of Threat Modelling
To integrate STRIDE effectively into your development process, it is essential to adopt a systematic approach:
- Define the Scope:
Begin by mapping out the system architecture, data flows, and key functionalities. This step sets the stage for identifying critical components that require protection. - Identify Threats:
Using the six STRIDE categories as a guide, systematically evaluate each component of the system. Document potential vulnerabilities and assess their likelihood and impact. - Develop Mitigation Strategies:
For each identified threat, design countermeasures that can either eliminate the risk or reduce its impact. This might include technical solutions (e.g., encryption, access controls) as well as process-oriented changes (e.g., user training, policy updates). - Review and Iterate:
Threat modelling is not a one-time exercise. Given the dynamic nature of software development, it is critical to review and update the threat model:- Annual Full Reviews: A comprehensive evaluation of the system’s threat landscape should be conducted at least once a year.
- Delta Threat Modelling: Every time significant changes are made—be it a new feature launch, architectural revision, or deployment model update—a focused threat modelling session should be conducted.
3. Tools and Best Practices
- Automation:
Integrate automated security testing into your CI/CD pipeline. Tools that provide continuous scanning and vulnerability assessment can catch issues as soon as they are introduced. - Collaboration Platforms:
Use collaboration and documentation tools that allow cross-functional teams to contribute to and review the threat model. This transparency not only improves the quality of the analysis but also ensures that security considerations become a shared responsibility. - Regular Training:
Organize workshops and training sessions to keep engineering teams updated on the latest threat modelling techniques and emerging security trends. Continuous education is vital for maintaining a proactive security posture.
Real-World Impact and Quantifiable Evidence
Empirical evidence underscores the business case for proactive threat modelling. Consider the following statistics and incidents:
- Phishing and Spoofing:
As phishing attacks become more sophisticated—thanks in part to AI automation—organizations have seen a marked increase in the success rate of these campaigns. Some reports have noted that well-crafted phishing emails can have a click-through rate that is 3 to 5 times higher than average, demonstrating the urgent need for robust identity verification and user education. - DoS Attacks:
The scale of DoS attacks is staggering. The 2017 Google incident, which involved spoofed traffic and reached 167 Mpps, is just one of many cases illustrating the potential disruption. With estimates of 12.5 million DDoS-capable devices reported in 2020 and a 133% increase in attacks recorded in 2022, it is clear that organizations must invest in scalable mitigation strategies to ensure service availability. - Elevation of Privilege:
Even minor oversights in access control can lead to critical vulnerabilities. Studies have shown that simple authorization flaws are among the top causes of security breaches, reinforcing the importance of integrating robust access control checks into every layer of your application.
These real-world examples and statistics highlight that the cost of not investing in comprehensive threat modelling is far higher than the cost of integrating it into the SDLC. For senior leaders, the message is clear: proactive threat modelling is not just about technical risk reduction—it is about safeguarding the organization’s reputation, customer trust, and overall business continuity.
Strategic Recommendations for Senior Technical Leaders
For CTOs and VPs of Engineering, implementing STRIDE threat modelling is as much about strategic vision as it is about technical execution. Here are some key recommendations:
- Adopt a Security-First Mindset:
Embed security into your organizational culture. Encourage every team member to think critically about potential vulnerabilities and to prioritize secure coding practices from day one. - Invest in Automation and Integration:
Utilize modern tools that integrate threat modelling with your existing development and deployment pipelines. Automation not only increases efficiency but also reduces the risk of human error in identifying vulnerabilities. - Customize and Evolve:
No single threat modelling framework is perfect for every scenario. Evaluate your organization’s unique risk landscape and consider integrating STRIDE with other methodologies (such as PASTA or VAST) to develop a hybrid approach that addresses both the technical and business aspects of security. - Measure and Iterate:
Establish key performance indicators (KPIs) and metrics to assess the effectiveness of your threat modelling initiatives. Regularly review these metrics, learn from past incidents, and continuously iterate on your threat modelling process. - Foster Cross-Functional Collaboration:
Security is a shared responsibility. Promote collaboration between engineering, operations, and even non-technical departments to ensure that every facet of the organization is aligned with the security strategy.
When Should You Hire Professionals
When the internal expertise or resources for comprehensive threat modelling are limited, engaging professional services can be a game changer. Organizations facing complex security challenges or undergoing significant digital transformation may benefit from the specialized skills offered by external experts. Software Secured Threat Modelling Services provide an experienced team to conduct in-depth analyses, tailor methodologies like STRIDE to your specific environment, and offer actionable insights to bolster your security posture. Leveraging their expertise can accelerate the identification of vulnerabilities, ensure industry best practices are followed, and ultimately safeguard your business from evolving cyber threats.
Conclusion
Adopting STRIDE threat modelling is essential for proactive, secure-by-design software development. By integrating continuous threat analysis into your SDLC, you not only reduce potential risks but also foster a culture of security awareness across your organization. In an era of increasing cyber threats, combining in-house efforts with professional services like Software Secured Threat Modelling can ensure your defenses remain robust and effective.

.avif)



.avif)