Comparing Website and Web Application Penetration Testing
Compare website vs. web application penetration testing. Discover the key differences, use cases, and how each enhances security, compliance, and customer trust.
TL;DR:
- Website penetration testing is crucial for identifying security vulnerabilities before hackers exploit them.
- Websites and web applications have different testing requirements based on functionality and complexity.
- Penetration testing involves steps like reconnaissance, exploitation, and reporting to ensure website security.
- Tools like Nmap, Burp Suite, and Nikto are used for comprehensive website penetration testing.
- Following best practices like regular updates and strong authentication can help secure websites against potential threats.
What is the difference Between a Website and a Web Application?
A website is typically a collection of static or dynamic web pages designed to convey information to users, such as news, blogs, or company profiles. Its primary purpose is usually informational or promotional, with minimal user interaction beyond navigation or form submissions.
In contrast, a web application is an interactive platform that allows users to perform specific tasks or access personalized features, such as logging in, managing data, or collaborating in real-time. Web applications are more complex, often involving dynamic server-side logic, user authentication, and rich user interfaces, examples being email services, online banking, and social media platforms. Essentially, websites focus on displaying content, while web applications emphasize user interaction and functionality.
What is Website Penetration Testing?
Website penetration testing is a simulated cyberattack on an organization's website, mostly a marketing website. The testing aims to learn where security weaknesses exist before bad hackers find their way through those vulnerabilities. This approach helps simulate attacks to detect vulnerabilities like SQL injections, cross-site scripting (XSS), and any potential threats that may compromise a site's security and integrity.
Why Is Website Penetration Testing Critical to Your Business?
Envision the implications of awakening one morning to discover that the personal information of your customers has been compromised or misused, or that an individual has successfully defaced your website. Such events can significantly damage your organization’s reputation and may also result in various legal, compliance, and financial complications. To mitigate these risks, regular penetration testing is essential. This proactive approach is designed to identify and rectify security vulnerabilities, thereby preventing potentially detrimental scenarios from occurring.
Common Vulnerabilities Found in Websites
Websites can harbour various hidden dangers. Some common vulnerabilities include:
- SQL Injection: Attackers exploit database queries to access or manipulate data.
- Cross-Site Scripting (XSS): Malicious scripts are injected into web pages viewed by other users.
- Cross-Site Request Forgery (CSRF): Users are tricked into executing unwanted actions on a trusted site.
- Unpatched Software: Outdated plugins or platforms can serve as entry points for hackers.
By identifying these issues, we can strengthen your website's defences.
Distinction Between Website and Web Application Penetration Testing
Even if they are both accessed using the same medium, there is still a distinction between websites and web applications according to their functional deployment requirements and complexity. It helps ensure that the correct methodologies are used for both.
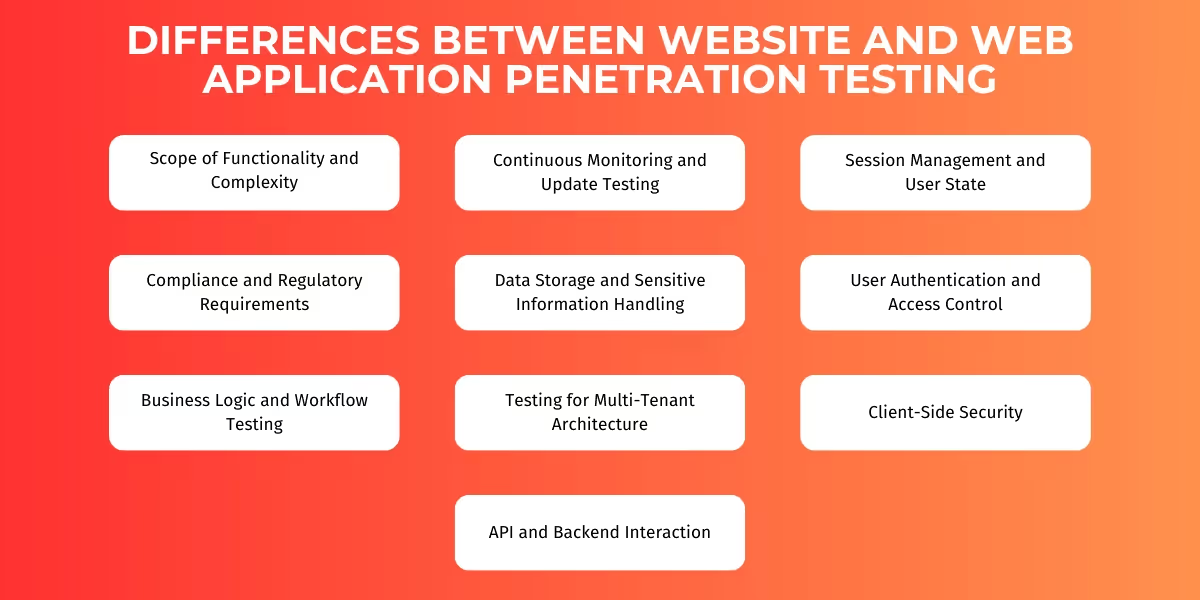
Scope of Functionality and Complexity
- Website: Generally more static and limited to information content or simple interactions such as a form submission. Testing focuses on identifying vulnerabilities in publicly accessible pages and distance from unauthorized access to other higher privileged areas. Most commercial websites are built on pre-existing frameworks such as WordPress.
- Web application: usually far more complex. In this case, interaction is user-driven, and users have application accounts, data storage, and transactions. Testing focuses on functionality within application workflows, permissions, data integrity, and complex backend interactions.
User Authentication and Access Control
- Website: This may not involve complex user authentication beyond basic login or simple forms. The login mechanisms are tested for strength against brute-force or credential-stuffing attacks.
- Web Application: It has multi-role access control (admin, user, guest) with significant authentication mechanisms. Testing includes role-based access control, privilege separation, and protection from privilege escalation and session hijacking.
Data Storage and Sensitive Information Handling
- Websites typically store limited sensitive data. Testing centers around securing minor data storage, such as contact forms or cookies, and ensuring that sensitive information is not unintentionally exposed.
- Web Applications usually store large amounts of sensitive user data, such as profiles and transaction records. Testing focuses on data encryption, secure storage, and appropriate access restrictions, including compliance with privacy standards like GDPR or HIPAA.
Business Logic and Workflow Testing
- Website: Lacks complex business logic and is primarily information-focused. Testing might involve checking for basic issues like Open Redirect vulnerabilities or minor form workflows.
- Web Application: usually includes complex workflows and business logic that can be exploited. Testing involves validating the correct functioning of transactions and whether hackers can bypass them for financial gains, accurate pricing calculations, and user permissions to reveal unique business logic flaws.
API and Backend Interaction
- Website: Usually doesn't interact heavily with APIs or backend systems. Testing might include checking for insecure API endpoints if part of a larger network.
- Web Application: Relies heavily on APIs or GraphQL to interact with backend systems, making API security a significant focus. Testing assesses API endpoints for unauthorized access, data validation, rate limiting, and injection vulnerabilities.
Session Management and User State
- Website: May have minimal session management. Testing includes checking for issues like open redirects or basic cookie security.
- Web Application: Requires robust session management to maintain a secure user state across interactions. Testing evaluates session duration, timeouts, secure cookie attributes, and protection against session fixation or hijacking.
Client-Side Security
- Website: Testing for common vulnerabilities like cross-site scripting (XSS), especially where user input exists. Client-side interactions are simpler and more limited.
- Web Application: Uses extensive client-side code for interactivity. Testing includes assessing client-side vulnerabilities like XSS, JavaScript injection, information leakage and insecure client-side storage.
Testing for Multi-Tenant Architecture
- Website: Typically doesn't require multi-tenant functionality, serving a single group of users accessing the same information.
- Web Application: Often multi-tenant, where clients share the same application and database instance. Testing includes checking for tenant data isolation and verifying that resources and permissions are within designated boundaries.
Compliance and Regulatory Requirements
- Website: May have limited compliance requirements related to basic data protection laws. Testing ensures secure handling of minimal data collection and enforcement of privacy policies.
- Web Application: Falls under more stringent compliance requirements depending on the data processed. Testing focuses on adherence to standards like PCI-DSS, HIPAA, and GDPR, particularly around data handling and access control.
Continuous Monitoring and Update Testing
- Website: Requires less frequent testing due to infrequent updates. Routine vulnerability scanning may suffice between major updates.
- Web Application: Undergoes frequent updates and feature additions. Regular penetration testing is essential for each major release to ensure new features don't introduce vulnerabilities.
The 7 Steps and Methodology of Website Penetration Testing
Understanding the steps involved demystifies the process and highlights its importance.
A. Reconnaissance
This stage is all about understanding the website and its different functionality. Meetings with the client and pen test provider help ensure that all parties are well-informed about the test. At this point, the test environment must be ready.
B. Development of Custom Scripts to Assist with Testing
The fun begins. Pen testers start diving deep into the website with a mix of manual and automated approaches.
C. Checking Platform's Plugins
Most commercial websites are built using frameworks like WordPress, Joomla, or more modern options such as WebFlow and Wix. The primary risk in this situation comes from plugins and additional components installed on these frameworks, which third-party developers often develop. The pentester would check the plugins used and whether they have well-known vulnerabilities.
D. Identification of Zero-Day Vulnerabilities
When critical vulnerabilities are identified, the client is notified immediately. The steps to reproduce the issue are shared with the client so their development team can begin remediation immediately.
E. Exploitation & Escalation
The less severe vulnerabilities found during the early stages of the pen test are exploited and escalated as much as possible without affecting the function of the website (for instance, if a pen tester is testing a vulnerability and it risks taking down the entire site, they’ll take it as far as possible without creating any actual harm). Test environments and test accounts are created to prevent any real damage and exploitation of the live application.
F. Cleanup & Reporting
Upon completion, penetration testers will gather all issues found, regardless of severity, and put them into a report. A good penetration testing provider should also include steps for replicating the issue so that the client’s development team can mitigate it.
G. Retesting & Certification
After the report is delivered, the client may patch several vulnerabilities. A quality pentest provider can retest these known vulnerabilities shortly after to verify that they have been fixed correctly or sufficiently. In some cases, the pen tester may require the client to develop a complete fix; in other cases, a “band-aid” solution may suffice for critical issues that need deeper attention later.
Tools Used in Website Penetration Testing
Several tools assist in making the testing process thorough:
- Nmap: A network scanner for discovering open ports and services.
- Burp Suite: A platform for testing web application security.
- Nikto: A web server scanner that detects dangerous files and outdated server software.
- Burp Suite: A set of tools used to test web applications for penetration.
- ZAP (Zed Attack Proxy): A dynamic application security testing tool published under the Apache License
These tools, combined with expert knowledge, ensure a comprehensive evaluation.
Web Regulation Compliance for Websites
Complying with regulations such as GDPR, HIPAA, and PCI-DSS is not only to avoid penalties but also to build trust in users. Penetration testing is done to ensure that a website complies well with the above standards by identifying and repairing deficiencies.
Securing Your Website with the Best Practices
Security is not a task but an ongoing commitment. Below are some best practices:
- Regular Updates: Keep your software, plugins, and platforms current.
- Strong Authentication: Add an additional layer of security by using multi-factor authentication.
- Encrypt Data: Use SSL/TLS certificates to encrypt data transmitted between the user and your site.
- Monitor Activity: Regular monitoring through logs and user activities will help to detect suspicious happenings early.
The above paves the way to a safer environment for business and its users.
How Software Secured Can Help Protect Your Website
At Software Secured, we focus on delivering exceptional penetration testing solutions tailored for growing companies like yours. We recognize that many businesses operate within limited budgets, so we provide premium penetration testing services at a reasonable price. Protect your assets without compromising your finances.
Our team conducts thorough testing tailored to your website's specific needs. We provide clear, actionable reports and work with you to implement solutions. Protecting your business and customers is our mission.
Ready to secure your website against potential threats? Contact Software Secured today to book a consultation.

.avif)